
Organizations today face mounting pressure to protect sensitive data while navigating increasingly complex regulatory landscapes. Microsoft Purview helps organizations classify information using AI-driven sensitive-info detection and govern retention, audit, and compliance rules consistently across environments.
However, moving from legacy information management systems to Purview's modern capabilities requires careful planning and execution. This guide outlines practical migration strategies that address the most common pain points IT leaders face during this critical transition.
Before configuring policies, you need clarity on what you're protecting, who needs to be involved, and how your current environment is structured. If you haven't completed your legacy feature audit yet, start with our Week 2 Guide: Audit Legacy Features for Purview.
Assessment foundations to have in place:
Understanding licensing distinctions is critical for migration planning. Misalignment here causes failed deployments and frustrated stakeholders. It's also recommended to confirm that you have the applicable licenses for the modern features.
Critical licensing decisions:
Action: Document which Purview features each policy requires, then map against your current licensing. Flag any gaps before configuration begins.
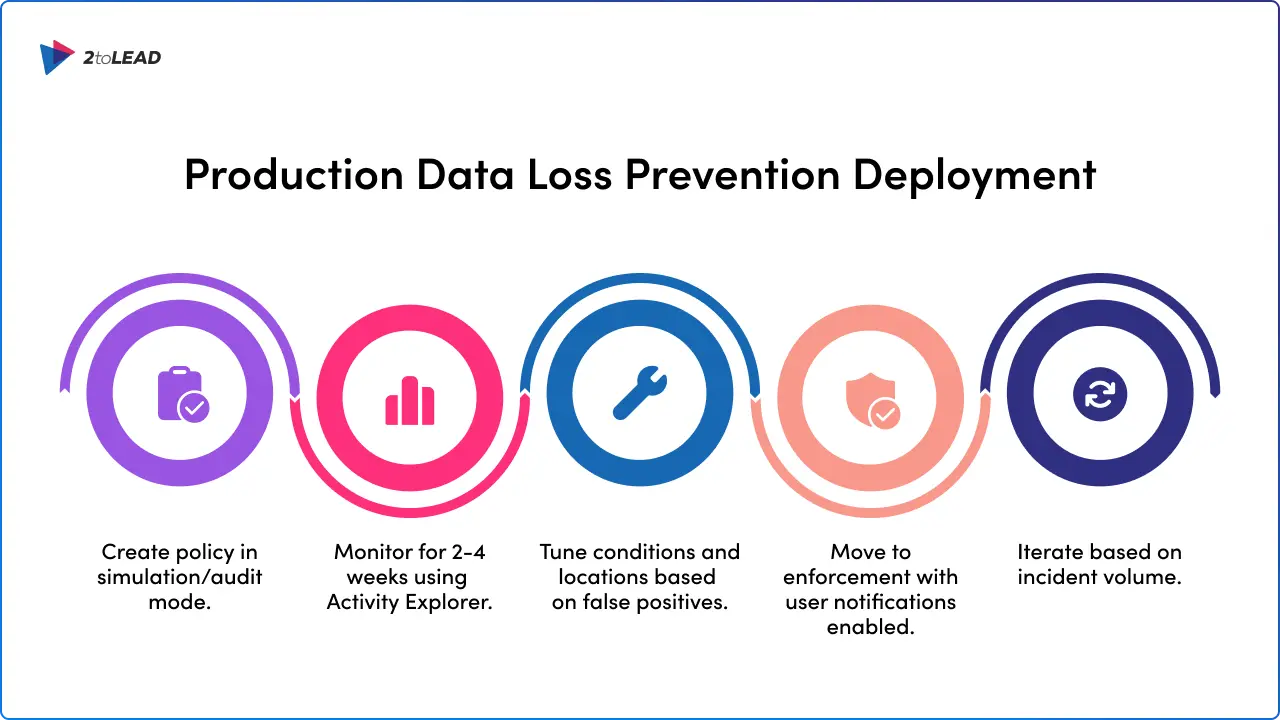
With your audit complete and licensing confirmed, DLP configuration is your first implementation priority. Start in simulation mode, then progress to enforcement.
DLP policy creation workflow:
Platform constraints to plan around:
Deployment sequence:
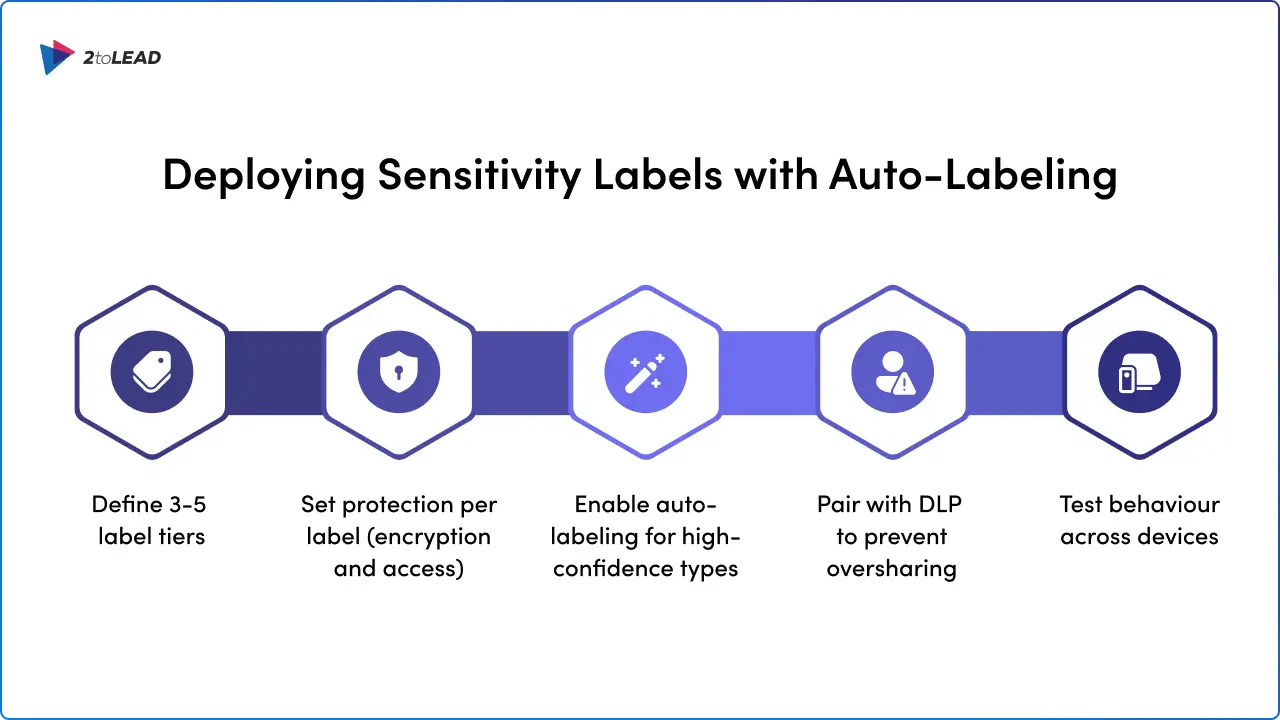
Sensitivity labels protect data at rest and in transit. Your implementation should balance user-driven labeling with automated classification.
Purview Information Protection classifies and labels data automatically, applying sensitivity labels that control access, encryption, and sharing permissions across SharePoint, Teams, OneDrive for Business, and beyond.
Why automation matters:
You no longer rely on employees remembering to label documents correctly; policies happen in the background, reducing human error. Sensitive customer data stays protected even if it leaves your environment.
Implementation checklist:
Pro tip: Start auto-labeling in simulation mode on 2-3 high-risk document libraries. Review recommendations before enabling automatic application.
Retention configuration replaces legacy Information Management Policies. The process involves creating labels, then publishing them to locations.
Making retention labels available to people in your organization so that they can classify content is a two-step process: Create the retention labels. Publish the retention labels by using a retention label policy.
Adaptive vs. Static Scopes:
Decide before you create your retention label policy whether it will be adaptive or static. If you decide to use an adaptive policy, you must create one or more adaptive scopes before you create your retention label policy, and then select them during the create retention label policy process.
Publishing workflow:
Configuration without validation is incomplete. Use Purview's built-in tools to verify policies are working before decommissioning legacy controls.
Verify that your new features are working as expected: Wait for the applicable time period for your new features to take effect. Confirm policies applied to a location using policy lookup. Use activity explorer to review actions related to labeling content. Use content explorer to review labeled items. Check the policy status for errors.
Activity Explorer capabilities:
Activity explorer lets you monitor what's being done with your labeled content. Activity explorer provides a historical view of activities on your labeled content.
Available filters include:
Predefined filter sets for quick validation:
Validation checklist:
You've completed the awareness phase, the audit phase, and now the implementation phase. The next step is to operationalize your new Purview environment for ongoing governance.
At its core, Microsoft Purview is about giving businesses visibility and control over their information. Think of it as the nervous system for your data: it connects policies, compliance requirements, and classification labels across the many applications your people use every day.
Ready to put these strategies into action? We've compiled our proven migration framework into a step-by-step resource designed for IT leaders navigating their Purview journey.
Inside you'll find:
Take the guesswork out of your migration. Get the playbook and start building your modern data governance foundation today.
Join Our Newsletter