
You’re an IT pro in a small or mid-sized business, responsible for keeping SharePoint, OneDrive, and Microsoft 365 Copilot safe without drowning your users in friction. You need a clear, practical way to classify data, apply the right protections automatically, and make sure Copilot doesn’t surface the wrong thing to the wrong person.
This guide demystifies Microsoft Purview’s classification capabilities and sensitivity labels, shows how they actually work with SharePoint and Copilot, and lays out a pragmatic rollout plan that fits an SMB’s time and budget.
Data classification helps you identify and understand sensitive content using tools like sensitive information types (SITs), trainable classifiers, and Exact Data Match (EDM). These detections power reports and policies across DLP, auto-labeling, and more. Microsoft provides a large catalog of built-in SITs, and you can create custom ones for your business needs.
Sensitivity labels define how classified content is handled. They travel with files and emails, can apply encryption, and add visual markings like headers or watermarks. Labels work across Microsoft 365 and many partner apps, enabling consistent handling without users memorizing policies.
Think of classification as what it is and labels as how we handle it.

SITs: Pattern-based detection for data like credit cards or bank accounts using checksums, keywords, and heuristics.
EDM: Matches exact values from a hashed reference dataset (e.g., member IDs) across SharePoint, OneDrive, and Exchange, reducing false positives for business-specific data.
Trainable Classifiers: Identify concepts like “Statements of Work” or “Board minutes” by learning from positive and negative examples. Microsoft offers pretrained models, and you can create custom ones for auto-labeling, DLP, or retention.
A sensitivity label can simply mark content, or it can enforce protection. With protection enabled, labels can restrict who opens a document, whether it can be copied or printed, and whether Copilot is allowed to extract content.

Because the label is embedded in the file’s metadata, protection travels with the content inside and outside your tenant. Labels are first‑class across Office on the web and desktop, and they integrate with SharePoint and OneDrive so collaboration and eDiscovery still work, even when encryption is applied with supported configurations.
There are a few tenant‑wide switches that make labeling “click” in SharePoint and OneDrive. First, enable sensitivity labels for Office files in SharePoint and OneDrive so the services can process labeled Office and PDF files. With supported encryption modes, the services can still index and coauthor documents in the browser while respecting the label.
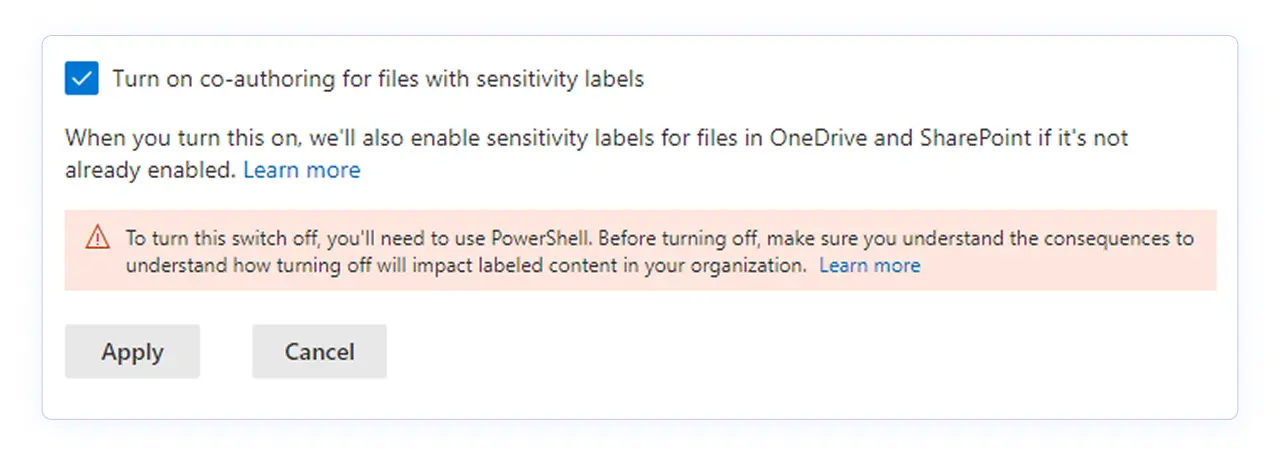
Second, turn on coauthoring for files encrypted with sensitivity labels so desktop real‑time collaboration and AutoSave continue to work on protected files.
Finally, consider setting a default sensitivity label for a document library so new or edited files don’t remain unlabeled.
Because Copilot honors existing permissions and label rules, user‑defined label permissions can outright block Copilot from reading a file’s contents.
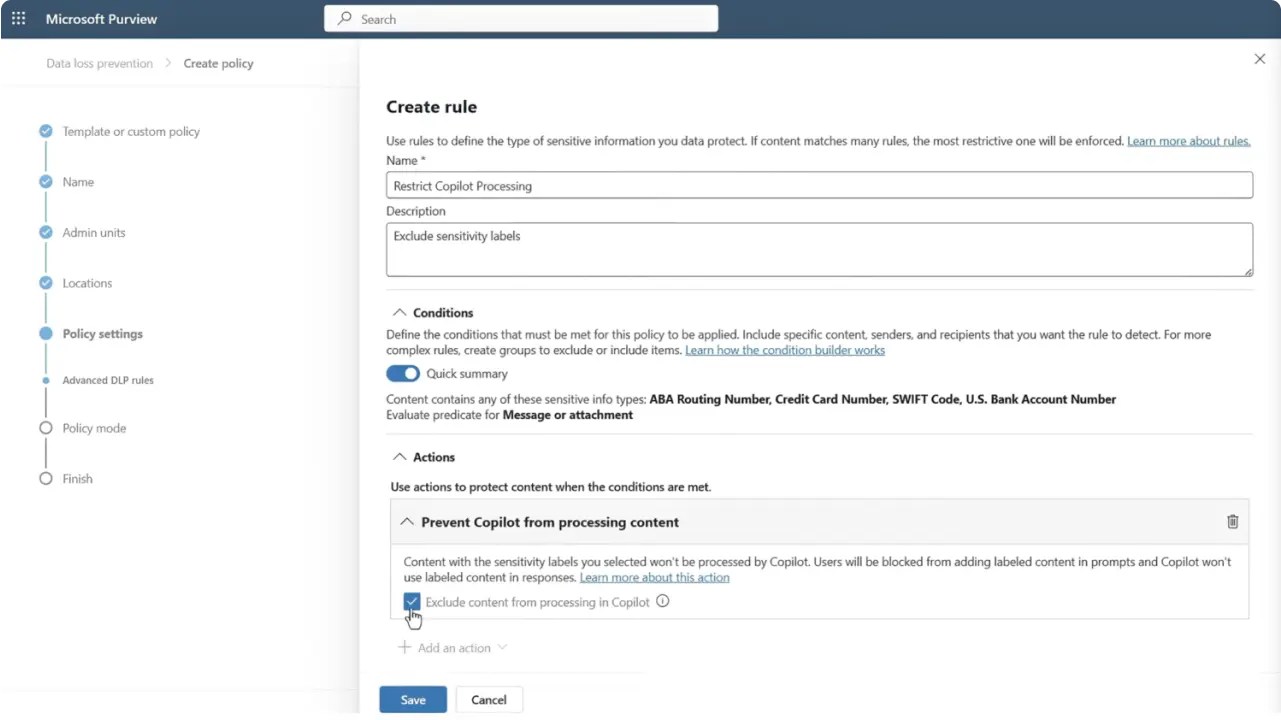
And if you need to be conservative while you get your arms around oversharing, Microsoft Purview DLP has a dedicated Copilot policy location that can prevent Copilot from using the content of items with certain labels in its responses, even if the item appears in citations.
As a separate, but related, governance lever, Restricted SharePoint Search lets you limit organization‑wide search and Copilot discovery to an allow‑list of vetted sites while you clean up permissions elsewhere. This doesn’t change item‑level permissions; it reduces discovery scope to lower exposure during a staged Copilot rollout. Use it to buy time, not as a permanent architecture.
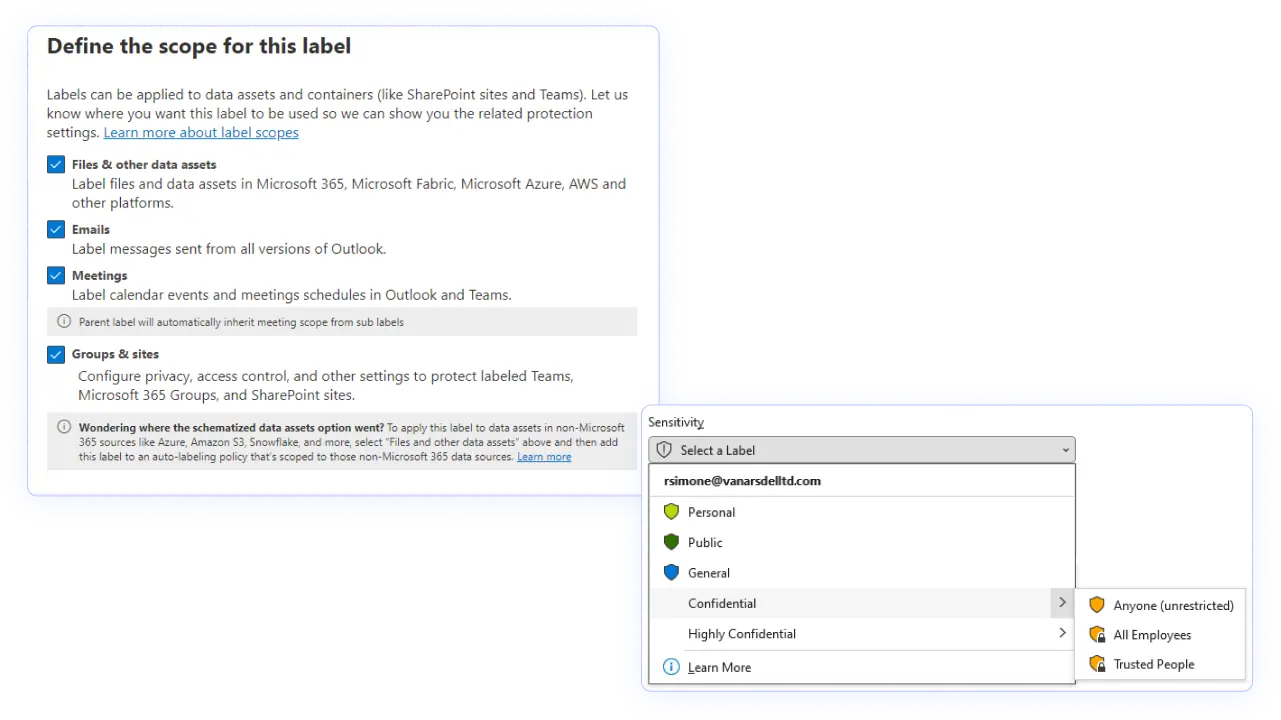
Beyond documents and mail, you can apply labels to containers: Teams, Microsoft 365 Groups, and SharePoint sites. Container labels set rules like public vs. private, guest access allowed or not, external sharing restrictions, default link type, and access from unmanaged devices.
They’re invaluable for governing collaboration spaces at creation time and throughout their lifecycle. Content inside a site or team does not inherit the site’s label, so you still need document‑level labels for granular protection.
SMBs succeed with fewer, clearer labels. Start with a four‑tier model that maps to business‑sensible handling rules: Public (no restrictions), Internal (baseline business content), Confidential (customer, employee, or financial data with limited sharing), and Highly Confidential (strictly need‑to‑know, encryption required).
Add sublabels when a department has special requirements, HR employee relations, Finance earnings materials, Legal privileged communications, so you can report and automate with more precision without flooding end users with choices.
Make one of your internal labels the default so unlabeled documents don’t slip through, and require justification to downgrade in your label policy to discourage casual weakening of protections while still allowing legitimate exceptions that are audited.
Copilot’s whole value is grounded in what each user is allowed to access. Labels strengthen that boundary in two ways.
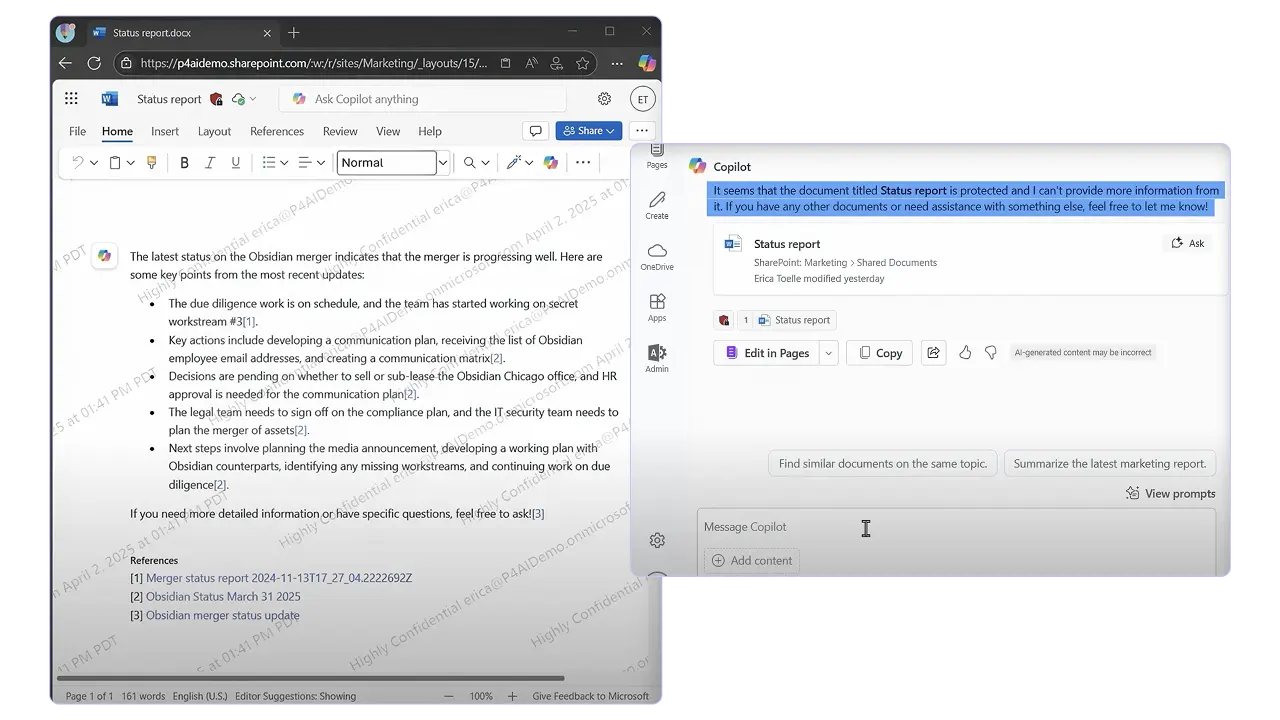
First, items with user‑defined label permissions can be unreadable to Copilot, preventing summarization from those files even if they appear in citations. Second, DLP for Microsoft 365 Copilot can be targeted to sensitivity labels, so you can explicitly prevent Copilot from processing content labeled Highly Confidential while allowing Internal or Confidential data to be summarized.
This lets you open up Copilot for the majority of your content while holding back critical pockets until you’re ready.
If you’re still remediating legacy oversharing, Restricted SharePoint Search helps narrow Copilot’s discovery scope to a curated set of sites while you fix broken permissions and normalize sharing practices elsewhere.
The end goal isn’t permanent restriction; it’s a phased, safe enablement: label broadly, reduce oversharing, then widen Copilot’s reach as your data estate improves.
A finance team publishing monthly results can work in a labeled SharePoint library where the default is Confidential, keeping drafts internal by default.
When the final pack is ready, a reviewer can upgrade it to Highly Confidential and restrict it to an executive group, so pre‑release numbers never slip into Copilot answers or search results.
A customer success team can protect customer lists using EDM, auto‑labeling any document that contains actual account numbers pulled from your CRM export, then rely on DLP to stop those files from being summarized in Copilot chats.
A legal team can train a classifier on “Statements of Work” to catch unstructured SOWs across old sites and apply a Confidential label automatically, ensuring future prompts don’t inadvertently surface proprietary terms.
Meaningful metrics aren’t complicated. Track label coverage across SharePoint and OneDrive libraries, aiming for steady increases in Internal and Confidential content with fewer unlabeled files. Watch downgrade and remove events in Activity Explorer to spot training or process issues. Keep a weekly pulse on DLP matches and Copilot blocked‑processing events for Highly Confidential labels; you should see spikes early as policies catch risky content, then a taper as users internalize new norms.
The most frequent mistake is a bloated label catalog. Too many near‑duplicates confuse users and drive inconsistent application. Start minimal, measure, and expand only for true business‑driven needs.
Another is turning on encryption everywhere too soon, which can frustrate coauthoring and third‑party workflows. Instead, enable coauthoring support for protected files and use encryption where it matters most. Teams sometimes assume a labeled site fully protects its files; remember, container labels set site behavior but do not label files inside, use default labels for libraries and auto‑labeling for coverage.
And if Copilot rollout is imminent, don’t rely on restricted search as a silver bullet; treat it as a temporary safety rail while you fix oversharing and improve labeling coverage.
Join Our Newsletter