
For organizations operating as managed service providers, data stewards, or multi-tenant SaaS vendors, sharing client data securely while maintaining operational simplicity has long been a balancing act. Traditional B2B collaboration approaches often create unwanted directory exposure and administrative burden. Microsoft Fabric's Cross-Tenant Access (CTA) for Providers offers a purpose-built solution that addresses these challenges head-on.
One of the most pressing concerns for IT leaders and security professionals managing multi-tenant data environments is the risk of exposing their internal directory to external parties. Traditional collaboration methods often require creating guest accounts that grant varying degrees of visibility into the provider's organizational structure.
Unlike B2B, use of cross-tenant access in Fabric warehouse items doesn't grant guests access to the provider's directory. This fundamental architectural difference means that when you enable external clients to query their data in your Fabric environment, you're not inadvertently opening doors to your broader organizational identity infrastructure.
The cross-tenant access feature allows provider tenants to share data stored in their Fabric warehouse items and SQL analytics endpoints with guest tenants. This feature is useful for organizations that need to share data with guest tenants. Consider a practical scenario: when company A stores Fabric data for company B, company B can use cross-tenant access to access their data in company A's Fabric tenant.
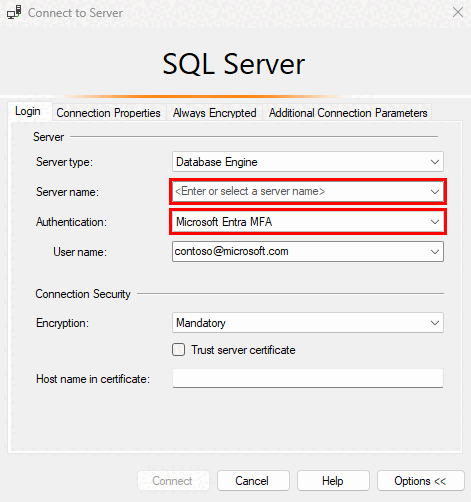
The authentication model reinforces this security boundary. Guests with permissions can access warehouse TDS endpoints using their own Entra ID identity credentials with tools such as SQL Server Management Studio (SSMS). To do that, guests authenticate with their home organization and are authorized to access a warehouse. This means your clients never need credentials issued by your organization; they use their existing corporate identities while you maintain complete control over what data they can access.
Identity management overhead represents a significant hidden cost in multi-tenant data operations. Every external user account requires provisioning, monitoring, and eventual deprovisioning. For providers managing dozens or hundreds of client relationships, this administrative burden scales quickly.
Cross-Tenant Access fundamentally shifts this responsibility. Providers don't need to manage individual guest users, when providers configure a group for cross-tenant access, the group membership is managed by the guest tenant. This delegated management model means your clients maintain their own user rosters when they hire new analysts or offboard departing employees, those changes flow through automatically without requiring tickets to your identity team.
When you enable guest principals for cross-tenant access, Fabric creates corresponding service principals for each guest in the provider's tenant, and groups for each guest group. This automatic provisioning eliminates manual account creation while maintaining the security controls you need.
The guest tenant is responsible for creating and managing Microsoft Entra groups and principals that are configured for cross-tenant access. By placing group membership control in the hands of your clients, you create a self-service model that scales efficiently while maintaining clear accountability boundaries.
Not every organization your business serves will have invested in Microsoft Fabric. For managed service providers and data platform vendors, this creates a practical challenge: how do you deliver value from your Fabric-based analytics infrastructure to clients using different technology stacks?
Unlike the external data sharing feature in Fabric, which allows providers to share OneLake data in-place with another Fabric tenant, this feature allows providers to share warehouse items with guests that don't have Fabric. This distinction is critical for providers whose client base includes organizations at varying stages of cloud and analytics maturity.
The access mechanism relies on familiar SQL connectivity patterns. Guest principals will access the cross-tenant warehouse item by using a TDS endpoint and will need a connection string to the warehouse. The provider must provide this connection string to the guests. Your clients can connect using industry-standard tools like SQL Server Management Studio, Power BI Desktop, or any application that supports TDS connections no Fabric subscription required on their end.

Guests with permissions can access data warehouse endpoints using their own Entra ID identity credentials with tools such as SQL Server Management Studio (SSMS). To do that, guests authenticate with their home organization and are authorized to access data warehouse endpoints. This flexibility enables you to serve a diverse client portfolio without requiring technology standardization across your customer base.
Successfully deploying Cross-Tenant Access requires clear understanding of the shared responsibility model between provider and guest organizations. As the provider, your obligations center on configuration, permission grants, and coordination with your clients.
The provider must grant a workspace role or permissions on the warehouse to these service principals. This permission model follows Fabric's standard security constructs, meaning your existing governance processes for workspace access can extend naturally to cross-tenant scenarios.
Before any technical configuration, establish a trust relationship with your client. Ensure the guest tenant consents to use cross-tenant access feature with your (provider) tenant. Guest tenants must follow the steps listed in Cross-tenant access for guests.
To use cross-tenant access for Fabric data warehouses with a specific provider tenant, the guest tenant must consent by following the steps listed in this document. Once a guest tenant consents to use cross tenant access with a specific provider, the provider can start granting guest principals access to warehouses. This consent-based model ensures both parties explicitly agree to the data sharing relationship.
Importantly, providers can choose to grant or remove access at any point of time. Your organization maintains full control over access even after the initial configuration. When consent is revoked, guests lose access to warehouses in the provider tenant within a day. However, existing sessions are unaffected.
Current Availability Note: Cross-tenant access for Fabric Data Warehouse is in a limited preview for providers. To register as a provider of cross tenant data, fill out the Cross-tenant access in Fabric DW Limited Preview Form. Organizations planning to leverage this capability should engage early with the preview program to influence the feature's development and prepare their environments.
Join Our Newsletter