
If you’re an SMB IT pro responsible for SharePoint and Copilot, you’re already juggling projects, permissions, and production incidents. You don’t need another tool, you need ANSWERS: Where is sensitive data stored? Who touched it? Which policies are working, and which are just noise?
Microsoft Purview compliance analytics can tell you where sensitive data lives and what to fix quickly, and in a format, you can share with leadership or auditors without spending weekends exporting CSVs.
This guide shows you how to use Purview’s insights to make practical, data‑driven decisions for SharePoint and Microsoft 365 Copilot. We’ll walk through the dashboards that matter, the signals to trust, and the simplest path to get those signals into Power BI when you want deeper analysis.
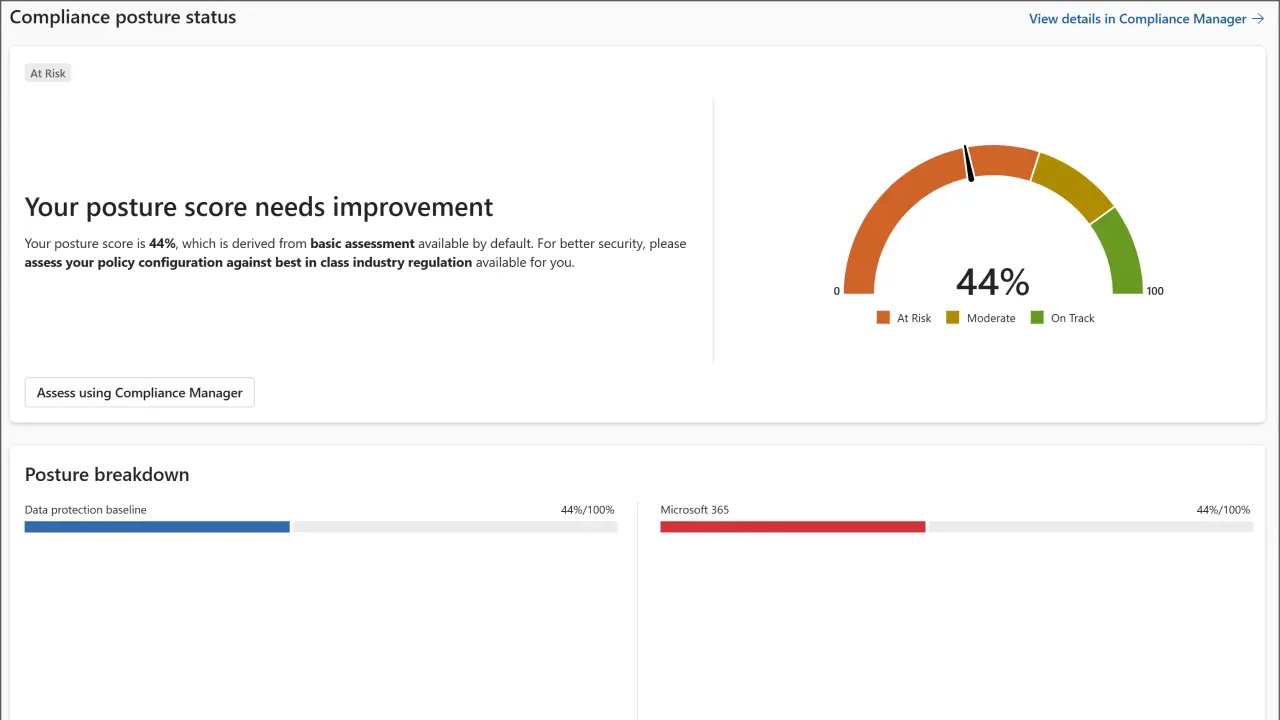
The clearest place to begin is Compliance Manager dashboard, a risk‑based dashboard that distills hundreds of controls into a single compliance score. That score isn’t a vanity metric; it’s tied to prioritized “improvement actions” so you can move the number by doing the work that lowers risk fastest. For a resource‑constrained SMB, this turns “boil the ocean” into a sequenced to‑do list.
Use the overview to establish your baseline9, then drill into action categories that align with your SharePoint and Copilot rollout. If your score shows gaps around data classification, harden label publishing and auto‑labeling. If DLP is the weak link, switch focus to rules and alert tuning. Treat the score as your north star for quarterly planning; it’s the one number execs tend to remember.
Practical KPIs you can defend to auditors and executives
Focus on KPIs that show both protection and productivity:
Activity Explorer is your operational lens. It aggregates events from audit logs, label applied, label changed, auto‑label simulations, and even file reads, across SharePoint, OneDrive, Exchange, and Office apps.
Filter by location to isolate SharePoint sites and OneDrive libraries, then trend “label downgraded” or “removed” events to spot risky behavior that policy tips might not catch. Run auto‑label simulations before enforcing preview impact without disruption.
If you don’t currently have advanced Purview licensing, you can still pilot these insights by enabling the 90‑day Purview solutions trial and validating value with a limited scope of sites. That’s the most budget‑friendly route for SMBs to prove the case.
When leadership asks, “where does sensitive data actually live?”, Content Explorer answers with evidence. It lets authorized reviewers browse by sensitivity label or sensitive information types and drill into items by location. This is invaluable for triaging oversharing in SharePoint or reviewing Copilot readiness. Access is intentionally strict, use the built‑in Content Explorer List viewer and Content Explorer Content viewer roles to separate “can see locations” from “can see item contents.” Keep those memberships tight to reduce insider risk and audit questions later.
DLP should be tuned, not merely turned on. In Purview, DLP includes an Activity Explorer view tailored to DLP events with filters that spotlight policy matches, overrides, and false positives. Out of the box you’ll see the most recent 30 days, which is enough to identify noisy rules, retrain users with targeted tips, and validate whether SharePoint‑specific conditions (like external sharing) are truly being caught.
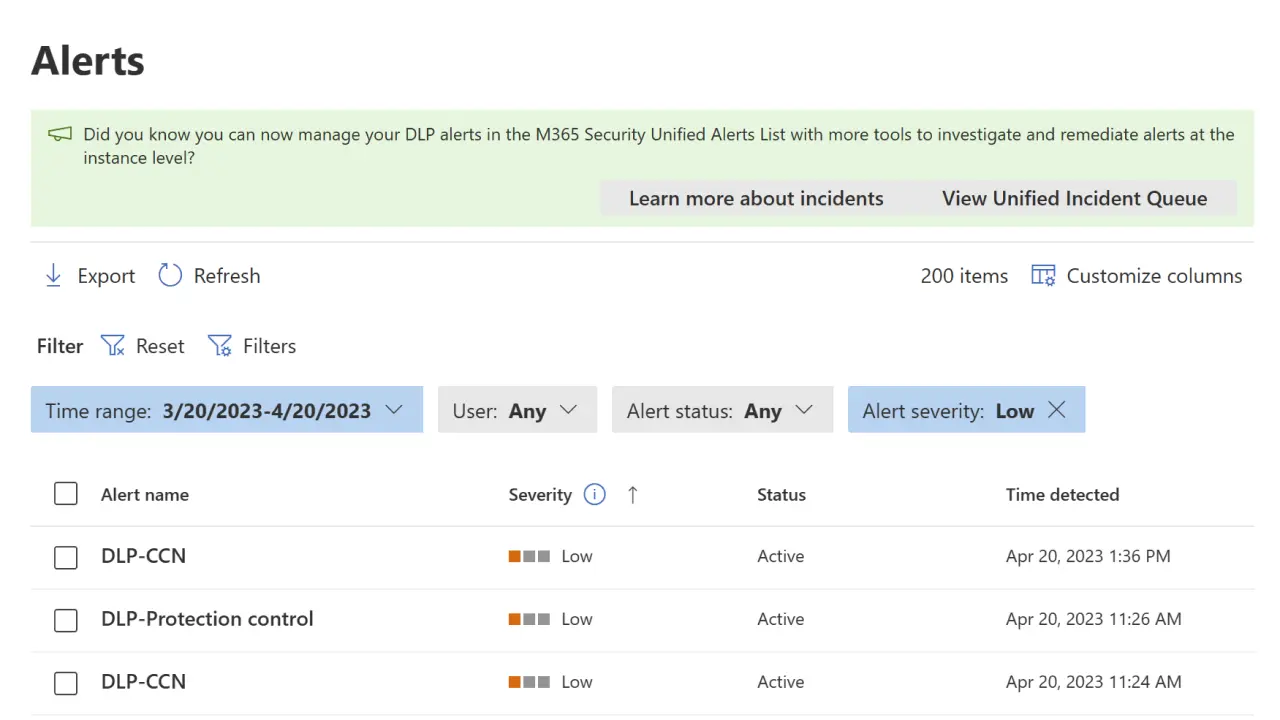
For investigations and operations, the DLP Alert management dashboard centralizes incident triage so you can review patterns instead of clicking through individual emails and files.
If Power BI is part of your analytics culture, remember that Purview DLP now extends to Microsoft Fabric and Power BI workspaces, enabling consistent policy logic across BI assets as well as SharePoint content. Plan capacity accordingly because some DLP capabilities require Premium workspaces.
Every meaningful decision eventually runs through audit evidence. Purview Audit (Standard) lets you search unified audit records for 180 days, while Audit (Premium) adds retention policies up to 10 years, higher‑value events, and faster access to logs; capabilities that matter when contractual or regulatory duties extend beyond the default window.
Use the newer search experience for saved searches and faster queries, and configure retention policies based on services, users, or activities so long‑term storage is deliberate and cost‑conscious.
For practical operations, set a weekly ritual: export a slice of key SharePoint and Copilot events, review spikes, and track mean time‑to‑close for DLP alerts. This habit builds muscle memory for incident response and produces an audit trail of your governance program’s effectiveness.
Copilot can make relevant content easier to discover; that’s a gift and a governance challenge. Purview provides several controls and reports tailored to AI interactions:
The net effect is straightforward: keep labels meaningful and widely adopted, aim DLP where it matters, and use DSPM reports to prove that Copilot usage remains inside your organization’s risk appetite.
For SharePoint owners, a few patterns consistently predict trouble. Watch the trend of “Applied/Changed/Removed sensitivity label” events for document libraries where oversharing occurs; sudden spikes in downgrades often precede incidents.
Use site and group sensitivity labels to control external sharing and conditional access at the container level, then confirm in reports that activity aligns with the intended access model. Finally, correlate DLP matches with sites that allow “anyone” links to verify whether policy is compensating for permissive sharing or just generating noise.
Most SMBs can live in Purview’s native dashboards. When you need a custom “Compliance Insights Hub,” you have two pragmatic data paths:
While you’re at it, govern the analytics layer itself: apply Purview sensitivity labels to Power BI content and consider DLP for Fabric/Power BI to create consistent protections from source to semantic model to report.
In your first 30 days, enable auditing, review Compliance Manager for a baseline, and turn on the Purview trial if you need advanced insights. In days 31‑60, formalize label strategy, simulate auto‑labeling, and tune DLP with a tight feedback loop between Activity Explorer and incident reviews. By day 90, export a minimal set of audit events and DLP alerts to Power BI for trend reporting, and light up DSPM’s Copilot reports to validate that AI is accelerating work without increasing exposure. You’ll have baseline Microsoft Purview compliance analytics in Power BI plus repeatable Audit insights for SMB IT.
Purview isn’t just a console; it’s your operating system for compliance signals. Compliance Manager tells you what to fix first, Activity and Content Explorer show where and how data is handled, DLP reports prove whether your guardrails work, and Audit preserves the evidence.
For Copilot, DSPM turns AI governance into a set of clear recommendations and measurable reports. Start with the built‑ins, export what you need to Power BI when the questions get sophisticated and keep your posture and productivity moving in the same direction.
--------------------------------------------------
Do we need E5 for all of this?
Not for everything, but some analytics, like deeper Activity Explorer insights and longer audit retention, are associated with advanced Purview capabilities. If you don’t have them, use the 90‑day Purview trial to prove value and scope costs before you commit.
Will Copilot expose sensitive data?
Copilot respects sensitivity labels and encryption. With DLP’s Copilot policy location you can exclude highly sensitive items from being processed in responses. Pair that with DSPM’s AI reports and you’ll both prevent and verify appropriate AI behavior.
Can we get everything into one dashboard?
Yes, export unified audit data and selective Purview signals to a store your BI team trusts, then model a curated star schema in Power BI. Add Power BI ActivityEvents for usage specificity and apply labels/DLP to the BI assets themselves.
Join Our Newsletter