
For ISVs and service providers building multi-tenant SaaS solutions, secure data sharing across organizational boundaries has long been a governance nightmare. Managing guest user sprawl, maintaining tenant isolation, and enabling customer self-service access typically required complex B2B configurations and administrative overhead. Microsoft Fabric's Cross-Tenant Access (CTA) for Providers offers a streamlined alternative that addresses these pain points head-on.
Traditional approaches to cross-tenant data access create significant friction for both providers and their customers. B2B guest invitations lead to directory bloat, permission management becomes unwieldy at scale, and customers often struggle with unfamiliar authentication experiences.
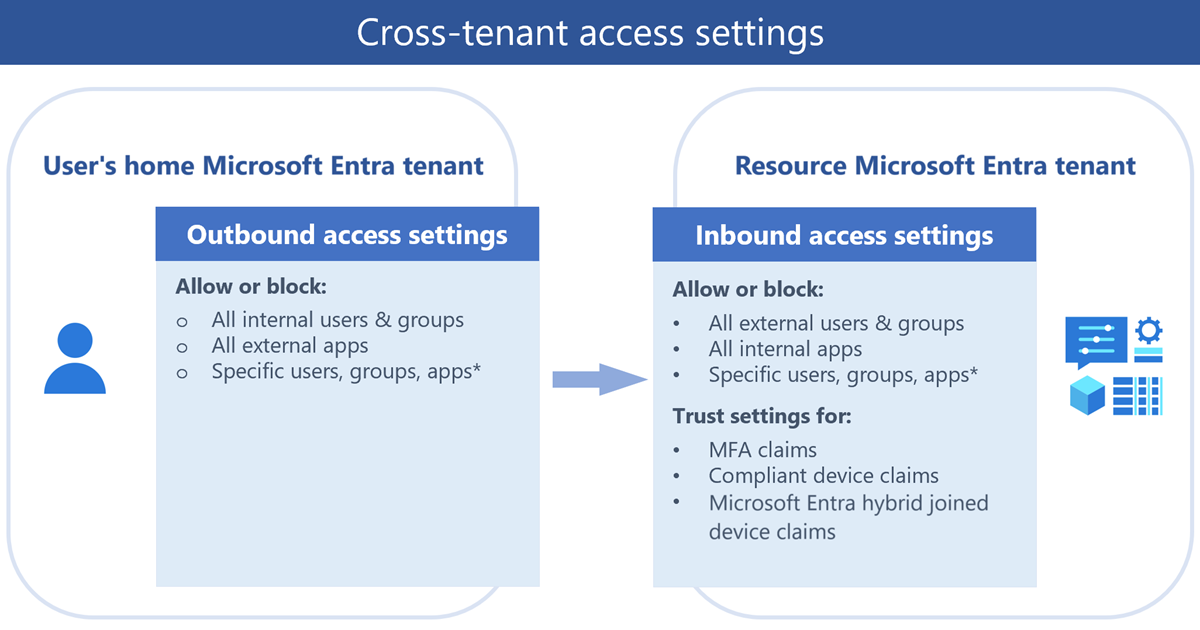
The cross-tenant access feature allows provider tenants to share data stored in their Fabric warehouse items and SQL analytics endpoints with guest tenants. This feature is useful for organizations that need to share data with guest tenants. For example, when company A stores Fabric data for company B, company B can use cross tenant access to access their data in company A's Fabric tenant.
What makes CTA fundamentally different from legacy approaches is its architecture. Unlike B2B, use of cross-tenant access in Fabric warehouse items doesn't grant guests access to the providers directory. Providers don't need to manage individual guest users, when providers configure a group for cross-tenant access, the group membership is managed by the guest tenant.
This shift in responsibility is crucial: your customers control their own user access, while you maintain control over data permissions and tenant isolation.
One of the most significant operational benefits of CTA is how it handles identity management behind the scenes. When the provider enables principals from the guest tenant to use this feature, Fabric creates corresponding service principals for each guest in the provider's tenant. The provider then grants permissions on the warehouse to these service principals.
This automated service principal management means you're not manually creating and maintaining guest accounts for potentially thousands of customer users. When you enable guest principals for cross-tenant access, Fabric creates corresponding service principals for each guest in the provider's tenant, and groups for each guest group.
For your customers, the experience feels native and secure. Guests with permissions can access warehouse TDS endpoints using their own Entra ID identity credentials with tools such as SQL Server Management Studio (SSMS). To do that, guests authenticate with their home organization and are authorized to access a warehouse.
This means customers use familiar SQL tools, authenticate with their existing corporate credentials, and benefit from their organization's security policies all without requiring a Fabric license on the guest side.

Implementing CTA requires careful attention to governance on both sides of the relationship. The consent model establishes clear trust boundaries and data sharing agreements.
To use cross-tenant access for Fabric data warehouses with a specific provider tenant, the guest tenant must consent by following the steps listed in this document. Once a guest tenant consents to use cross tenant access with a specific provider, the provider can start granting guest principals with access to warehouses. Providers can choose to grant or remove access at any point of time.
Data teams should understand exactly what information flows between tenants. By providing consent, you acknowledge that certain elements of guest accounts are shared. These include email addresses, user principal names, group memberships, and directory identifiers. Provider tenant's terms and conditions govern the use of this data.
This transparency is essential for compliance. Both parties know precisely what data is exchanged to facilitate access, enabling informed decisions about whether CTA aligns with organizational policies.
From a revocation standpoint, the model provides reasonable protection. When consent is revoked, guests lose access to warehouses in the provider tenant within a day. However, existing sessions are unaffected.
Key governance responsibilities for providers include:
Guests retain critical responsibilities:
This division of labor allows customers to maintain their own security posture while providers focus on data governance and access control at the warehouse level.
Understanding where CTA fits in your overall Fabric architecture is critical for ISVs planning multi-tenant deployments. Unlike the external data sharing feature in Fabric, which allows providers to share OneLake data in-place with another Fabric tenant, this feature allows providers to share warehouse items with guests that don't have Fabric.
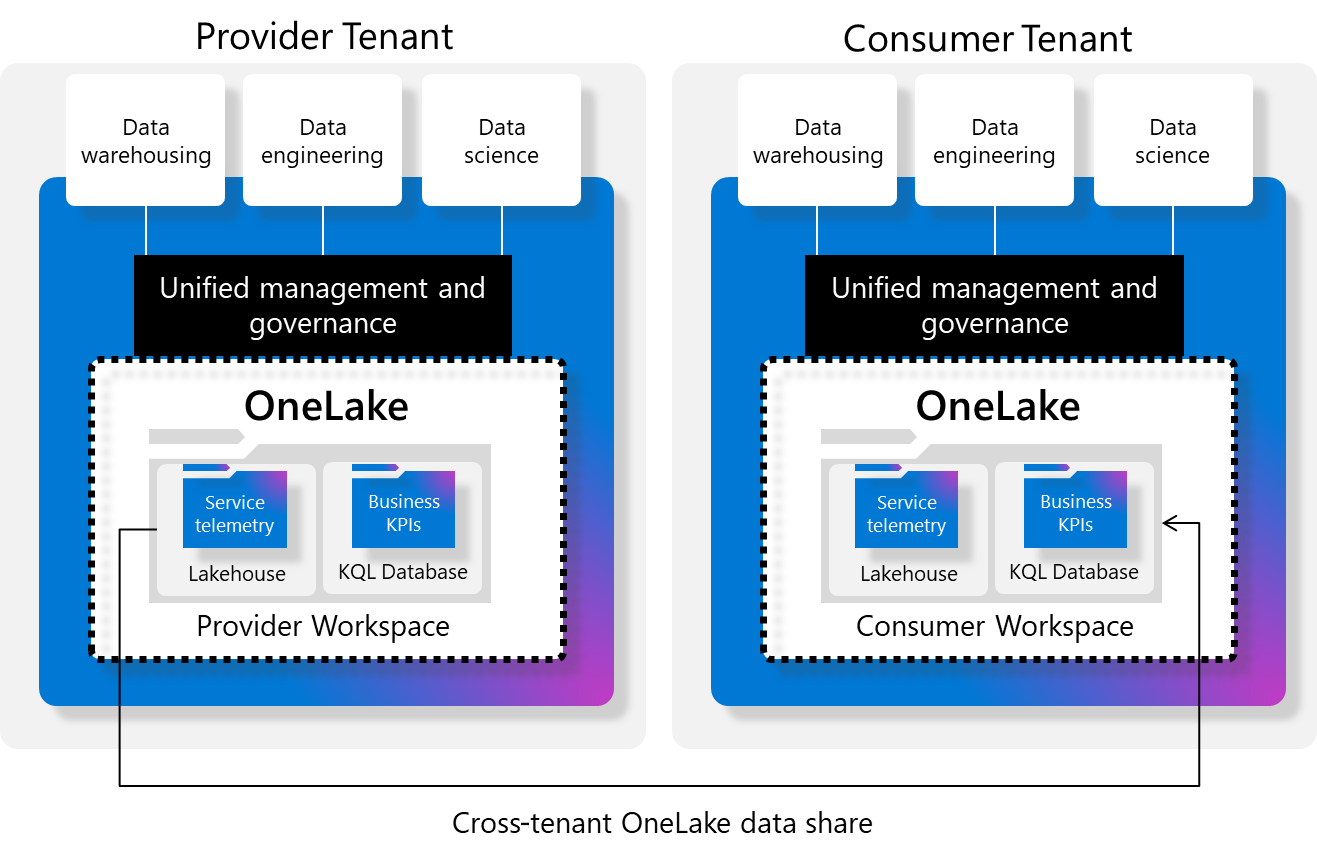
This distinction matters for architectural decisions. CTA is optimized for direct warehouse access scenarios where customers need to query structured data using SQL tools. External data sharing serves different use cases involving lakehouse and OneLake data.
Microsoft Fabric is an all-in-one analytics solution that covers everything from data integration to Machine Learning, real-time analytics and Business Intelligence. The big value proposition of Microsoft Fabric is a highly integrated, end-to-end, and easy-to-use service that simplifies your analytics. What is not being highlighted enough, is how compelling this platform really is for ISVs and SaaS creators that want to offer analytics to their customers, either as their main product, or as an add-on to the main offering.
For multi-tenant architectures, consider aligning CTA with workspace-per-tenant patterns. Use Entra groups from the customer tenant as your source of truth for access management. This approach lets customers manage their own group memberships while you control which groups can access which workspaces and warehouses.
Security teams should note that Programmatically granted permissions aren't subject to review or confirmation and take effect immediately. This underscores the importance of implementing least-privilege access and monitoring cross-tenant mappings through available APIs.
Cross-Tenant Access represents a significant step forward for multi-tenant SaaS data architectures on Microsoft Fabric. By centralizing data in your provider tenant while enabling secure, governed access for customers using their native identities, CTA eliminates traditional B2B complexity while maintaining the security and isolation that enterprise customers demand.
For organizations evaluating this capability, start by mapping your current multi-tenant access patterns and identifying which customer scenarios would benefit from direct warehouse access versus OneLake data sharing. Then work with your customers to establish the trust relationships and consent flows that CTA requires.
Join Our Newsletter