
Technology leaders exploring Microsoft 365, Copilot, Viva, or broader AI transformation are facing a new reality: attackers aren’t breaking in, they’re logging in and disrupting cloud at scale. Drawing from the latest Microsoft Digital Defense Report (MDDR) 2025, this guide turns threat intelligence into an outcome‑driven plan for Entra, Purview, Defender, Azure, and Copilot so you can “Love the way you work. Together™".
The implications for Microsoft tenants are direct: every organization must prioritize identity protection, cloud resilience, and data governance. These trends should directly inform how you deploy Microsoft Entra, Purview, Defender, Azure, and Copilot. The next budget cycle should focus on controls that actually reduce risk, not just check compliance boxes.
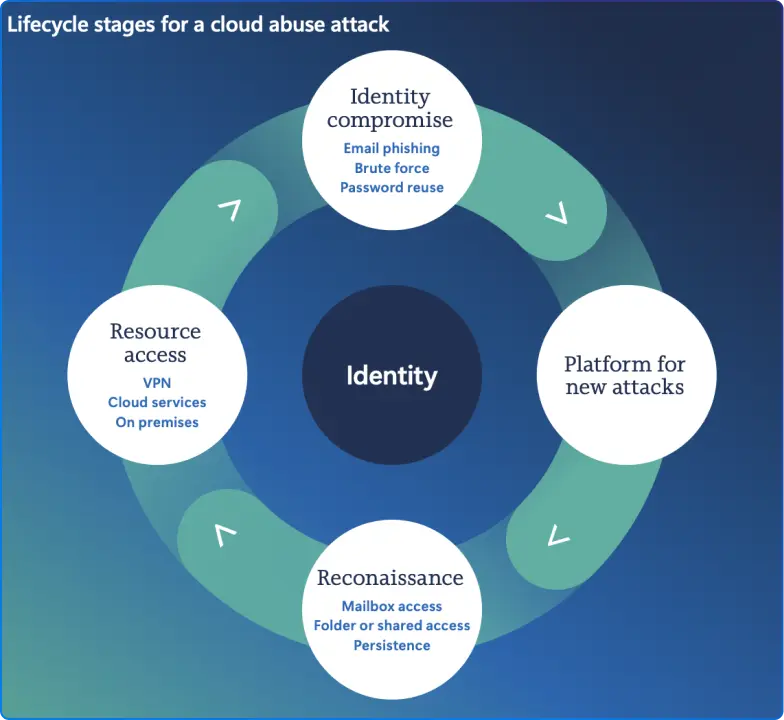
For years, security teams have focused on keeping attackers out. But the 2025 report reveals a new reality: instead of brute-forcing their way past firewalls, adversaries are increasingly exploiting legitimate credentials, tokens, and trusted relationships to quietly access systems and data.
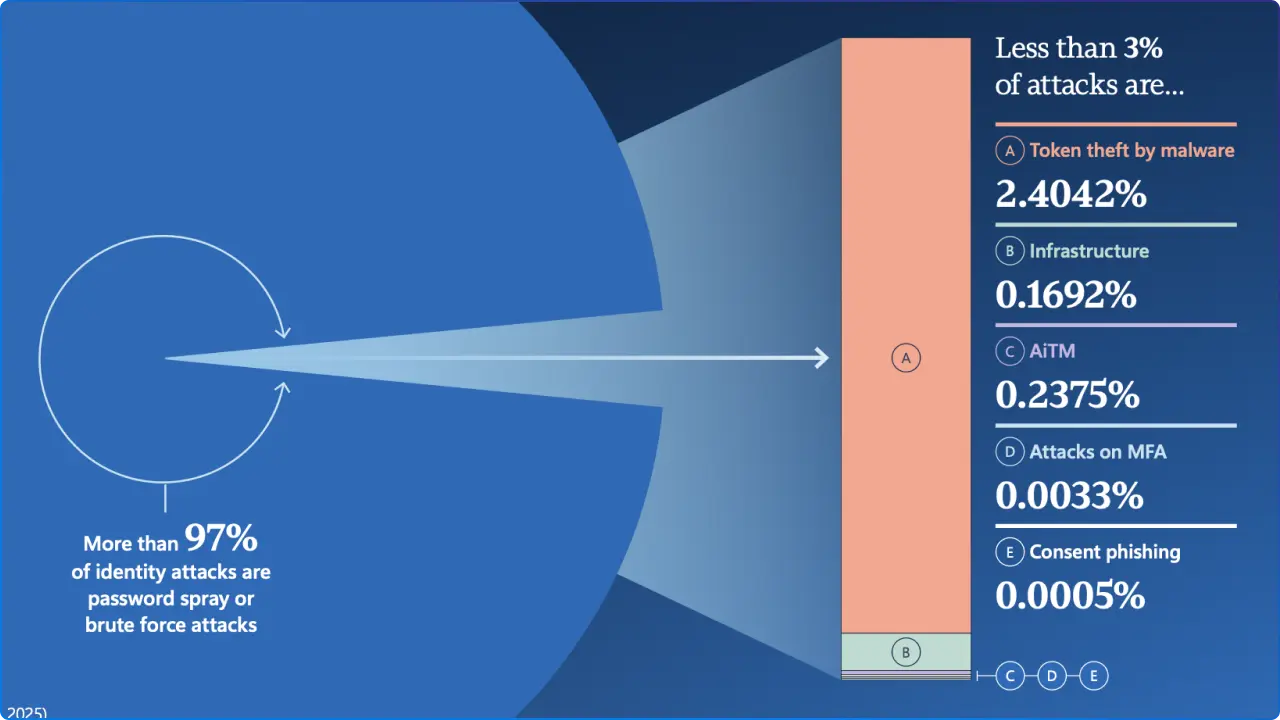
Modern MFA stops >99% of unauthorized access, but attackers pivot to token theft, OAuth consent phishing, AiTM, device code flow abuse, and elevated workload identities that lack strong governance. They’re logging in, not hacking in. This means every identity, human and non-human, must be governed, monitored, and protected as if it’s a potential entry point.
Microsoft Defender for Cloud telemetry shows a steep rise in credential access, collection, and impact alerts in Azure, with the most alarming trend being an 87% jump in destructive campaigns. Attackers aren’t just trying to persist quietly, they’re aiming to disrupt, destroy, and exfiltrate at scale. Hybrid ransomware is now mainstream, with over 40% of attacks involving both on-premises and cloud components.
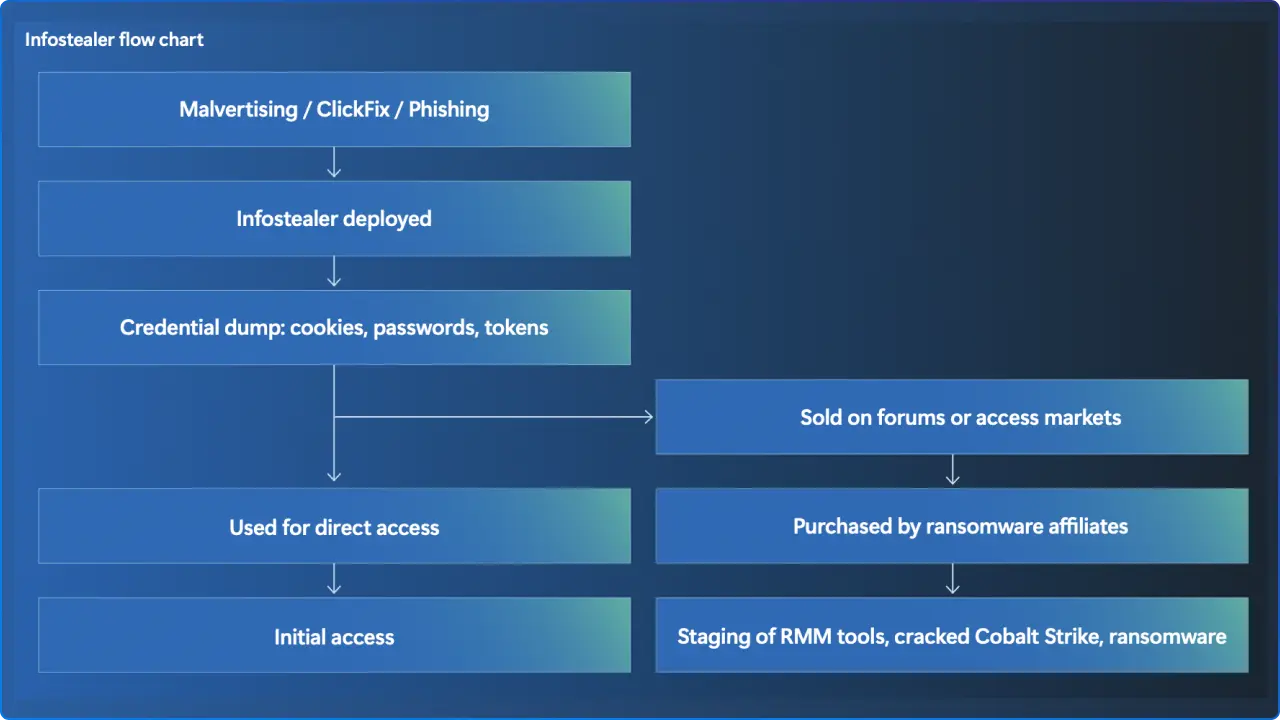
ClickFix, copy/paste to PowerShell/Run, was the #1 initial access method (47% of observed notifications). Here’s how it works:
Meanwhile, device code phishing is rapidly adopted across criminal and nation‑state actors. Attackers prompt users to enter device codes on fake portals, granting access to accounts and data. This technique is now appearing in Teams invitations, making it harder for users to spot fraudulent activity.

Threat actors use AI to automate social engineering, discovery, and evasion. Your own AI systems (Copilot, agents, plugins) are targets for prompt injection, tool abuse, and data leakage. Defending AI with AI is now a strategic imperative. Layered guardian patterns, SLM front-door filtering, deep LLM analysis, tool/telemetry correlation, are essential to secure extensions and data paths.
Our POV: Security, compliance, and employee experience win when they’re designed together, clear, outcome‑driven, and Microsoft‑savvy. We make controls practical for business leaders and humane for employees.
1) Verify explicitly (Identity‑first): Enforce phishing‑resistant Entra MFA, Conditional Access templates, and PIM for roles/groups. Govern workload identities (apps, service principals) as first‑class citizens with least privilege.
2) Govern data by default (Purview‑first): Auto‑classify what matters, turn on DLP across SharePoint/Teams/Exchange, enforce records, and watch insider risk. Design assuming exfil by default.
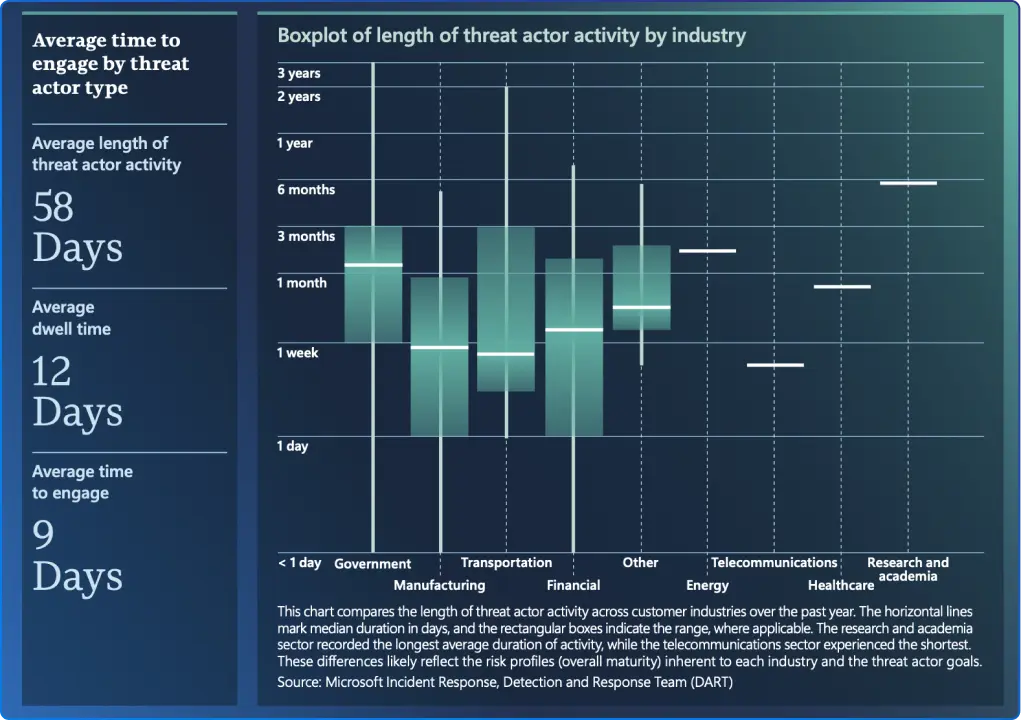
3) Resilience by design (Cloud & IR): Baseline Defender for Cloud, segment landing zones, isolate backups, and measure IR by time‑to‑engage and blast‑radius reduction.
4) Secure AI by design (Copilot & agents): Layer guardian patterns: SLM front‑door filtering → deep LLM analysis → tool/telemetry correlation; secure extensions and data paths.
5) Human‑centered hardening (awareness & EX): Neutralize ClickFix/device code with targeted comms, WDAC/AppLocker, and least‑privilege defaults across Teams/SharePoint/Viva.
Do now: Enforce phishing‑resistant MFA; deploy Conditional Access templates; enable PIM for roles/groups; disable legacy auth.
Next: App governance & consent reviews; full workload identity inventory/least privilege; continuous token monitoring
Do now: Auto‑label crown jewels; enable DLP for SharePoint/Teams/Exchange; insider risk policies for data movement.
Next: Records disposition at scale; eDiscovery readiness drills mapped to breach scenarios.
Do now: Defender for Cloud foundational hardening; attack path analysis; endpoint tamper‑resistance; WDAC/AppLocker to blunt ClickFix‑style execution.
Next: Hybrid ransomware playbooks; immutable backups; Key Vault secret rotation. Trends to watch: 87% rise in destructive campaigns, collection/impact spikes
Do now: Prompt/response filtering at the SLM front‑door, tool invocation allow‑lists, data boundary checks, full audit/logging.
Next: Guardian agents with decision gates; anomaly detection across agent orchestration + M365 telemetry; Responsible AI governance.
Value: Reduce blast radius and downtime across Azure resources.
Actions: Defender for Cloud baseline + CA/PIM for admins; isolate backups; simulate mass‑deletion response.
Outcome KPIs: High‑risk misconfigurations ↓; time‑to‑engage IR ↓; restore time verified.
Examples (transformation & benefits)
Value: Block token/OAuth abuse and workload privilege creep.
Actions: Force MFA enrollment; CA for risky sign‑ins; app consent reviews; workload identity least‑privilege.
Outcome KPIs: MFA coverage → 98–100%; risky sign‑ins ↓; stale app permissions ↓.
Examples:
Value: Prove data is governed—even if access occurs.
Actions: Purview classification at scale, DLP policies, insider risk watchlists for sensitive roles.
Outcome KPIs: % sensitive content labeled; DLP rule effectiveness; insider‑risk MTTR.
Examples:
Value: Ship AI benefits without opening new attack paths.
Actions: SLM front‑door filters; tool/connector allow‑lists; human‑in‑the‑loop for high‑impact steps; telemetry correlation.
Outcome KPIs: Blocked prompt‑injection attempts; zero unauthorized tool calls; successful red‑team test cases.
Value: Neutralize 2025’s top initial access methods.
Actions: Script block logging + clipboard‑to‑terminal monitoring; WDAC/AppLocker rules; Teams/Outlook comms kit.
Outcome KPIs: Reduction in copy‑paste execution chains; fewer device‑code auth anomalies.
Why this works: ClickFix was the #1 initial access vector (47%), and device code phishing surged late‑year and even appeared via Teams invites—both demand behavior + control changes, not just email filtering
The numbers from Microsoft’s 2025 Digital Defense Report aren’t just statistics, they’re signals that the threat landscape is changing faster than most organizations’ defenses.
Whether you’re leading IT, driving digital workplace transformation, or shaping business strategy, the message is clear: waiting is not an option.
The most resilient organizations aren’t those with the biggest budgets or the latest tools, they’re the ones that act early, learn fast, and build security into every layer of their digital workplace. That means challenging assumptions, reviewing controls, and making governance, identity, and AI safety part of your everyday conversations, not just annual reviews.
If you haven’t mapped your next steps, now is the time. Start with one use case, one KPI, or one conversation with your team. The threats are evolving, but so are the solutions and every action you take moves your organization closer to a future where people truly "Love the way you work. Together™".
What you get: A prioritized heat‑map across Identity, Data, Cloud, and Copilot; a 30‑day action plan mapped to Microsoft controls; and a board‑ready KPI starter set (MFA coverage, patch latency, time‑to‑engage IR, sensitive‑data coverage). Love the way you work. Together™.
Join Our Newsletter