
If you manage SharePoint and Copilot for a small or mid-sized business, you live at the intersection of collaboration and control. Your users want frictionless sharing and AI-powered assistance; your job is to ensure the right people see the right data, nothing more, nothing less. Microsoft Purview is the governance and protection layer that makes this possible. It brings together classification, labeling, data loss prevention (DLP), insider risk management, and targeted access controls so Copilot can be helpful without becoming a shortcut to overshared content.
This guide walks you through a pragmatic, SMB-ready approach to securing Microsoft 365 data, especially SharePoint and OneDrive, so your Copilot rollout is safe, compliant, and confidence‑inspiring.
Copilot is grounded in your organization’s Microsoft Graph data. It uses a user’s permissions and context to retrieve content from SharePoint, OneDrive, Teams, Exchange, and more, and then composes a response.
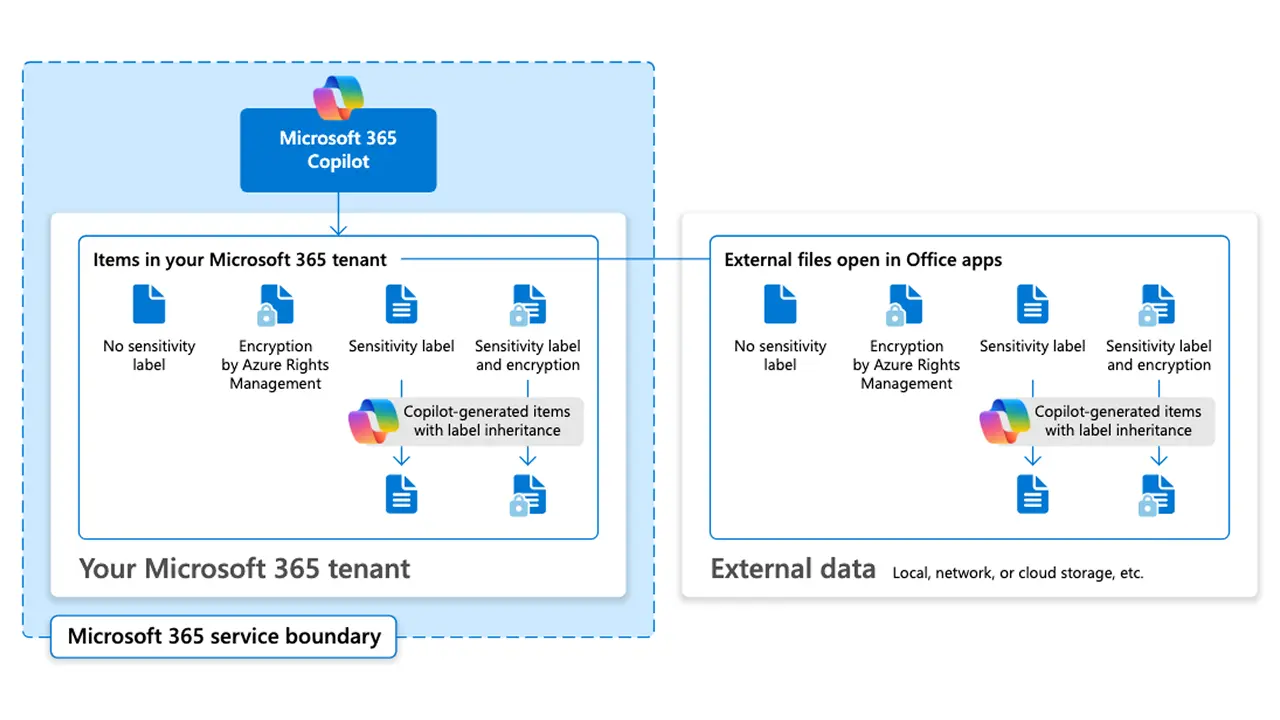
Copilot does not grant new access; it honors existing permissions and rights, including encryption from sensitivity labels. That means your security posture is only as strong as your current sharing model and label strategy. If a file is encrypted with usage rights, Copilot respects those rights. In fact, when labels apply encryption, the user must have the appropriate rights (such as VIEW and EXTRACT) for Copilot to summarize content at all.
This is the Copilot permissions model in action: responses are grounded by the Microsoft Graph and honor label‑applied encryption and site permissions end‑to‑end. For security teams evaluating Copilot data governance, the takeaway is simple: improve permissions and labeling, and Copilot will reflect that posture.

Start with a simple, durable classification model. Sensitivity labels in Microsoft Purview let you classify and protect data without getting in the way of work. Labels can apply encryption and visual markings to files and emails, and they extend to collaboration containers, Teams, Microsoft 365 groups, and SharePoint sites so that the security posture travels with the place where people work. For SMBs, a four‑to‑five tier label set (for example: Public, General, Confidential, Highly Confidential, Regulated) is usually plenty, as long as each tier drives clear behaviors and guardrails.

Labels don’t need to be purely manual. Auto‑labeling detects sensitive data patterns and applies labels at scale in SharePoint, OneDrive, and Exchange based on conditions you define. You can even set default labels for specific SharePoint document libraries to encourage the right behavior by design. Begin with a narrow pilot, apply auto‑labeling to a handful of high‑risk patterns like financial account numbers or government IDs, then expand once you’ve validated the match accuracy with your business stakeholders.
DLP is your policy engine for “data in motion” and “data in use.” Purview DLP monitors and can block risky actions like sharing outside the organization, copying to USB, printing, or posting to external apps.
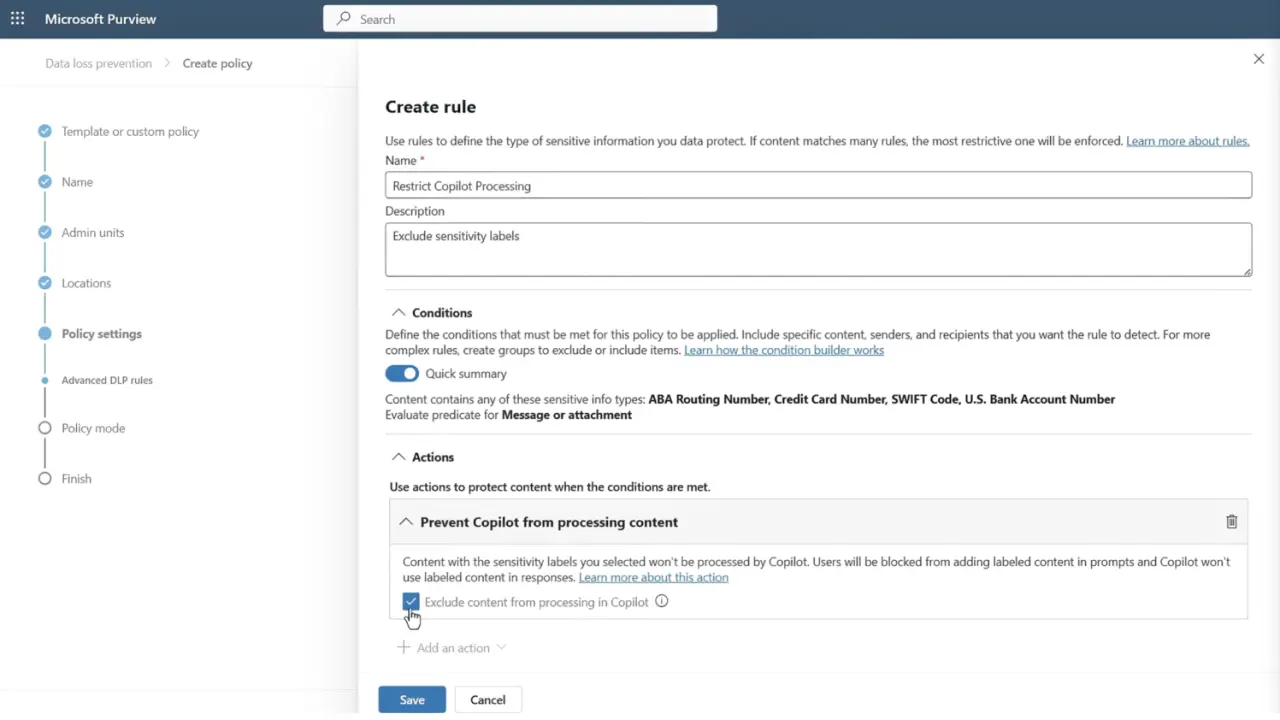
The same DLP policy framework now includes a dedicated Microsoft 365 Copilot location, allowing you to prevent Copilot from summarizing content with certain sensitivity labels or patterns, while still letting authorized users open those files directly. This is especially useful when you want Copilot to help with most work but never synthesize Highly Confidential or Regulated content into an answer.
Pro tip: Create a Copilot DLP policy using the Microsoft 365 Copilot policy location and target Highly Confidential (or Regulated) labels to block Copilot from summarizing sensitive data while still allowing citations for authorized users.
A common SMB concern is, “We want Copilot, but we’re still cleaning up oversharing.” You don’t have to choose between safety and speed.
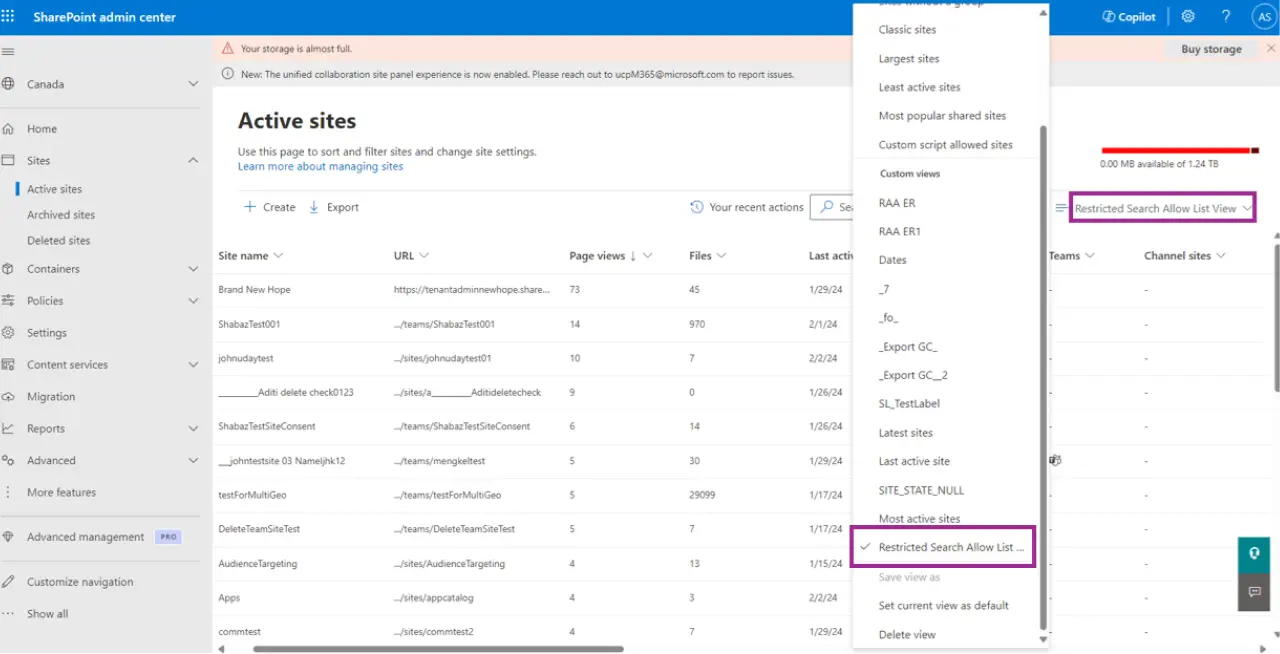
Microsoft introduced Restricted SharePoint Search to let you limit both enterprise search and Copilot experiences to a curated allowed list of SharePoint sites that you approve, while still honoring user‑level access to their own or previously accessed items. This approach effectively limits Copilot to trusted areas first, then gradually expands the allow list as data hygiene improves. Be aware that the allowed list is intentionally small, up to 100 sites, to keep you focused on your most trustworthy locations.
If you need a more granular posture for specific sites, Restricted Content Discovery provides a way to limit discoverability of chosen SharePoint locations. While similar in spirit, this control is tuned to keep certain sites out of broad search and discovery until you’re ready. Pair it with container‑level sensitivity labels and external sharing controls to create a layered defense.
Purview and SharePoint give you practical tools to find and fix oversharing. Data access governance reports surface sites with potentially overshared or sensitive content so you can prioritize remediation.

From there, Site access reviews in the SharePoint admin center involve site owners directly. You can initiate a review on flagged sites; owners receive a guided task to confirm whether wide access is required or needs to be tightened. This shared responsibility model helps your small IT team scale governance with the people closest to the work.
When a site truly must be locked down, Restricted Access Control lets you gate a SharePoint site to one or more Microsoft Entra security groups (or Microsoft 365 groups). Users need both explicit site permissions and membership in the restricted group to get in, which dramatically reduces the blast radius of accidental sharing. You can apply a similar “only people in these groups” policy to OneDrive at both the tenant and per‑user levels, ensuring personal storage for executives or sensitive departments stays appropriately ring‑fenced.
Not every device touching SharePoint is compliant. You can limit or block access from unmanaged devices while still allowing browser‑based work.
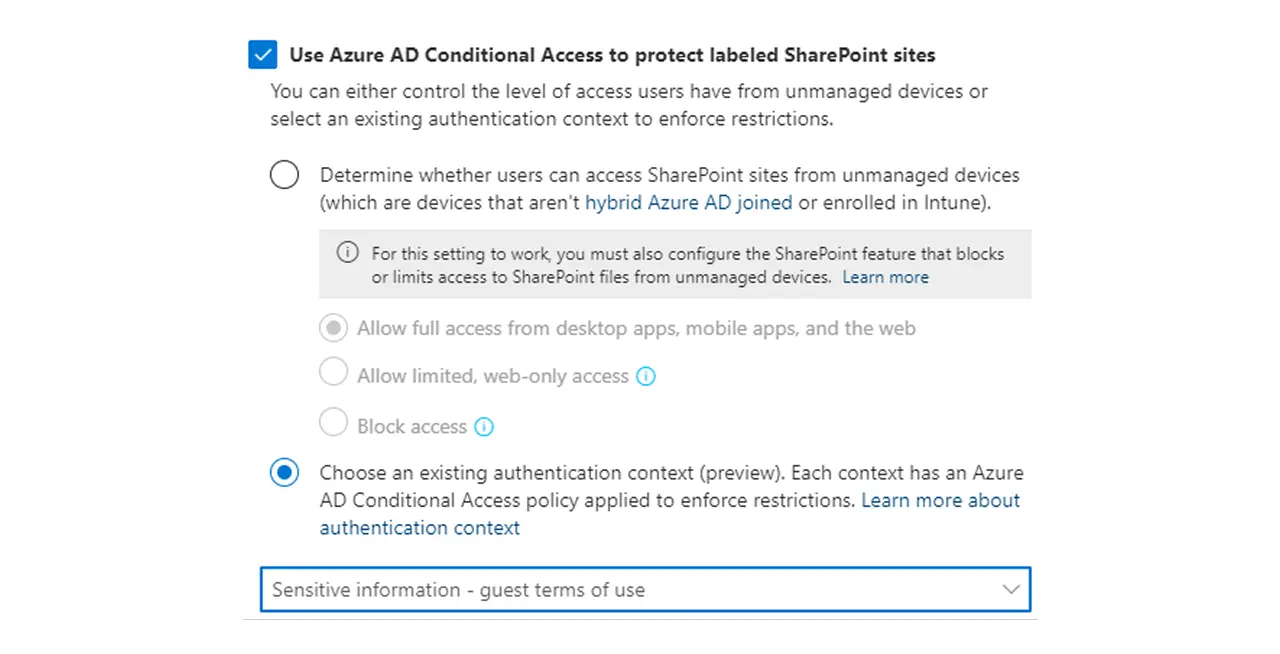
Using Conditional Access with app‑enforced restrictions, you can prevent downloads, copying, and printing from untrusted endpoints across SharePoint and OneDrive, which is especially valuable when Copilot surfaces a file preview in the browser. This control buys you time to onboard devices into management without halting collaboration.
As you roll out Copilot, adopt a “safe‑by‑default” stance for sensitive content. A pragmatic pattern for SMBs is to use DLP to exclude Highly Confidential and Regulated labels from AI summarization. Copilot can still surface a citation to the document so authorized users can open it in Office, but it won’t distill the content into a chat response.
This setting is made in the DLP policy using the Microsoft 365 Copilot location and a condition that targets the labels you want to shield. Combine this with label‑applied encryption and your most sensitive material remains protected even if someone tries to route around policy.
Not every data incident is malicious. Sometimes it’s a hurried employee moving a folder to the wrong site. Microsoft Purview Insider Risk Management helps you detect and investigate patterns like mass downloads, data exfiltration to personal storage, or repeated policy violations.
It is built with privacy by design (pseudonymization, role‑based access), and it integrates with eDiscovery (Premium) when escalation is required. Start with the out‑of‑the‑box templates for data leakage and IP theft, tune thresholds to your organization’s scale, and pair policy alerts with short enablement moments for managers so the response is corrective, not punitive.
Security improves when there’s fewer sensitive data lying around. Use retention labels and auto‑apply policies to ensure you keep critical records for the right duration and dispose of stale content that no longer serves a business purpose. Many SMBs see quick wins by assigning default retention labels to key SharePoint libraries and using auto‑apply rules for finance, HR, and legal repositories. This reduces the surface area Copilot and search can see and simplifies your compliance story.
Some organizations, especially in regulated industries or firms that handle client‑confidential work, must prevent collaboration between specific groups. Information Barriers in Microsoft 365 now extend to SharePoint, helping you enforce separation end‑to‑end so teams that shouldn’t interact don’t accidentally share files or discover each other’s content. Use this for scenarios like M&A due diligence, audit independence, or client‑specific walls.
A focused month is enough to establish a defensible baseline without boiling the ocean.
Week 1: Map the label taxonomy; identify your top ten business‑critical SharePoint sites; enable Restricted SharePoint Search to only those sites while you validate hygiene.
Week 2: Publish sensitivity labels to a pilot group; set default labels on a couple of sensitive libraries; create a DLP policy at the Copilot location to shield your highest tiers from summarization (citations still allowed).
Week 3: Run data access governance reports; kick off site access reviews; apply Restricted Access Control to the riskiest sites; document decisions.
Week 4: Turn on unmanaged device controls; roll out your first Insider Risk templates with conservative thresholds; send a short manager‑enablement note about what to expect. Result: a working safety net that supports Copilot rather than constrains it.
Closing guidance: Keep Copilot’s field of view small and trusted, make labels your lingua franca, use DLP to set bright‑line boundaries for AI summarization, partner with site owners for remediation, lock down crown‑jewel sites, and keep unmanaged devices on a short leash. Done together, Copilot becomes safer and more useful.
Security posture isn’t set‑and‑forget. Make auditing part of your ongoing rhythm. The Copilot data protection architecture guidance underscores auditing and access controls, and the Purview portals provide dashboards for policy matches, label adoption, and insider risk cases.
Review DLP match trends monthly, track which sites are on your Restricted Search allow list and why, and schedule quarterly site access reviews for high‑value repositories. This discipline is what turns point controls into a cohesive program.
For SMBs, the winning strategy is simple and layered. Start by keeping Copilot’s field of view small and trusted with Restricted SharePoint Search. Make labels the lingua franca of your data, and let auto‑labeling and default library labels do the heavy lifting. Use DLP to set clear boundaries for AI summarization so critical content never leaks through generated text.
Bring site owners into the remediation loop through data access governance reports and access reviews, and tighten the crown‑jewel sites with Restricted Access Control. All the while, keep unmanaged devices on a short leash and treat insider risk alerts as coaching opportunities, not witch hunts.
When you put these pieces together, Copilot becomes safer and more useful, and your SharePoint content grows more orderly over time. That’s the practical promise of Microsoft Purview: confident collaboration with governance that scales to the size of your team.
--------------------------------------------------
Does Copilot bypass permissions or encryption?
No. Copilot respects Microsoft Graph permissions and label‑applied encryption. If a user doesn’t have rights, Copilot can’t retrieve or summarize the content.
Can I stop Copilot from summarizing Highly Confidential content without blocking user access?
Yes. Use a DLP policy scoped to the Microsoft 365 Copilot location and target the appropriate sensitivity labels. Copilot can still show a citation, but it won’t summarize the file.
We’re still cleaning up oversharing—can we enable Copilot safely now?
Yes. Use Restricted SharePoint Search to limit Copilot and enterprise search to an allow list of trusted sites, then expand as you remediate. Users still interact with files they own or previously accessed. The allow list can include up to 100 sites.
How do we lock down a particularly sensitive SharePoint site or an executive’s OneDrive?
Apply Restricted Access Control (for SharePoint) and OneDrive access restriction policies so only members of specified Microsoft Entra or Microsoft 365 groups can reach the content, even if they were previously granted permissions.
What if we need to keep departments or client teams fully isolated?
Use Information Barriers with SharePoint to prevent collaboration and content sharing between defined segments.
Join Our Newsletter