
If you’re an IT pro running SharePoint and piloting or scaling Copilot inside a small or mid-sized business, you sit in the blast radius of two big forces: the explosion of unstructured content and the sudden acceleration of AI usage.
Microsoft Purview is no longer just a compliance checklist; it’s the operating system for data governance across Microsoft 365, your on‑prem estates, and crucially your AI interactions. This deep dive walks through practical, advanced use cases you can deploy now, along with near‑term trends that will change how you govern data over the next year.
SharePoint is still the backbone of your content services, but Copilot changes the game. Generative AI amplifies both productivity and risk because it can surface old, mis‑permissioned, or high‑sensitivity content faster than any human can.
Your governance posture must therefore extend beyond files at rest to prompts, responses, audit signals, and user risk, without strangling collaboration. Microsoft Purview gives you that bridge: labels that travel with content, risk-adaptive controls that get tougher only when behavior gets riskier, and AI-aware auditing and lifecycle controls for the prompts and outputs themselves.
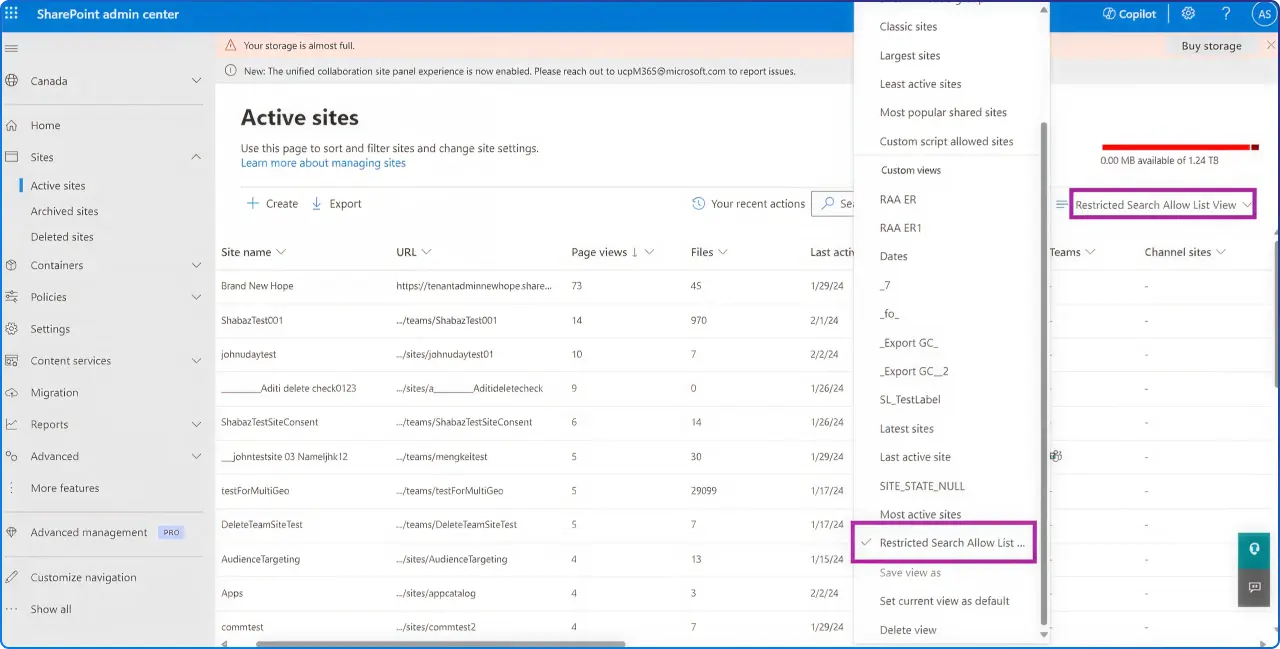
Features like Restricted SharePoint Search let you fence what Copilot and organization-wide search can reach until you finish the cleanup and labeling you’ve planned.
The fastest, lowest‑friction way to reduce oversharing risk as you roll out Copilot is to curate what search and AI can see. Restricted SharePoint Search allows you to limit organization-wide search and Copilot experiences to a specific allowlist of sites while still honoring file‑level permissions and owners’ access. This lets you migrate and label in phases without pausing your Copilot pilot.
You can keep high‑trust sites in the allowlist and move riskier legacy areas off the path until they’re remediated.
Container sensitivity labels then let you enforce site‑level protections, privacy, external sharing, unmanaged device access, and even default file labels, so the places where content lives enforce posture before a single file is created. That means your Microsoft 365 groups, Teams, and SharePoint sites carry their guardrails with them, which is enormously helpful in SMBs that don’t have heavy central provisioning.
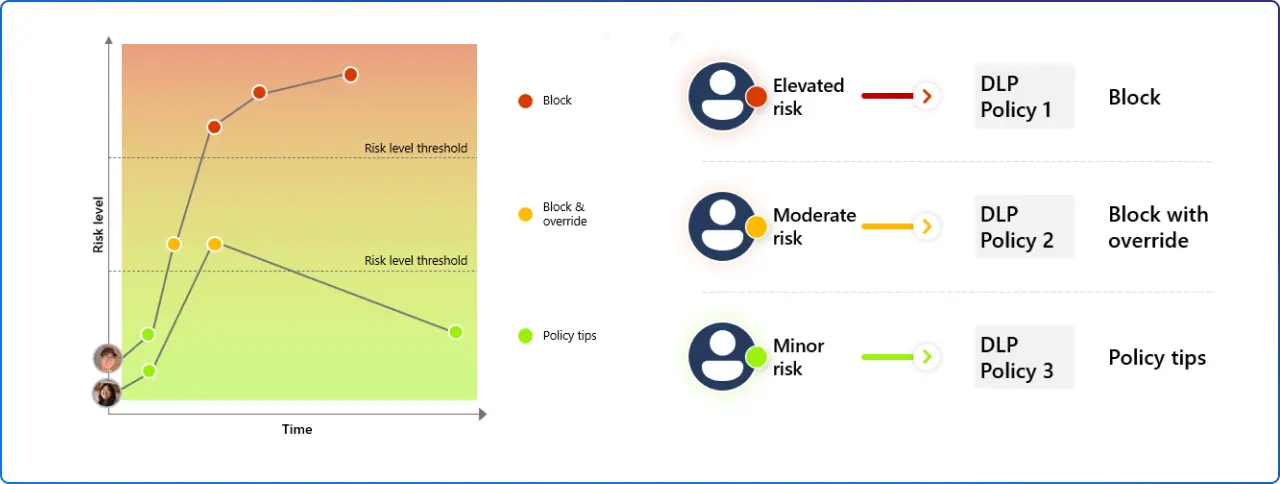
Static DLP policies create friction for everyone, even your safest users. Adaptive Protection DLP changes that by feeding Insider Risk signals into DLP so only high‑risk users receive stronger controls, like blocking uploads to unsanctioned cloud apps, clipboard actions, or printing, while low‑risk users work with minimal interruption. You’ll spend less time tuning exceptions and more time investigating real risk.
Pair this with Endpoint DLP to monitor and govern the ordinary actions that leak data, copy/paste, save‑as, printing, and browser‑based uploads right where they occur. For SMBs, endpoint controls are a force multiplier because they protect data the moment it leaves SharePoint or OneDrive, independent of the app.
You can even extend enforcement to on‑premises repositories. Purview’s on‑prem DLP and the Information Protection scanner can discover, classify, and label content across file shares and SharePoint Server, closing the loophole where legacy storage avoided governance.
Most SMBs are “accidentally multi-cloud.” A marketing team’s S3 bucket or a product analyst’s BigQuery dataset becomes part of your attack surface. Purview’s multi-cloud connectors let you register and scan Amazon S3 to profile and classify what lives there, while similar guidance covers Google BigQuery projects.
The point isn’t to replace native cloud tooling; it’s to create a unified data catalog and policy brain across your estate. Compliance Manager then helps you track controls across Azure, AWS, and GCP so you can answer audits without fire drills.
AI content creates new classes of records: user prompts, grounded responses, and generated summaries. With Purview Data Lifecycle Management, you can set retention policies specifically for Copilot and other AI app interactions, separate from Teams chats or email. That enables patterns like keeping normal chats for 90 days while limiting AI interactions to 30, crucial in regulated environments or IP‑sensitive teams.
When something sensitive slips into a prompt, eDiscovery Premium for AI data can search for and even delete Copilot prompt/response data across supported workloads. An advanced pattern for SharePoint: use retention labels that also serve as DLP conditions. For example, a “Contracts—Active” label can keep a document for seven years and prevent external sharing while the label is present, giving you lifecycle and exfiltration protection in one stroke.
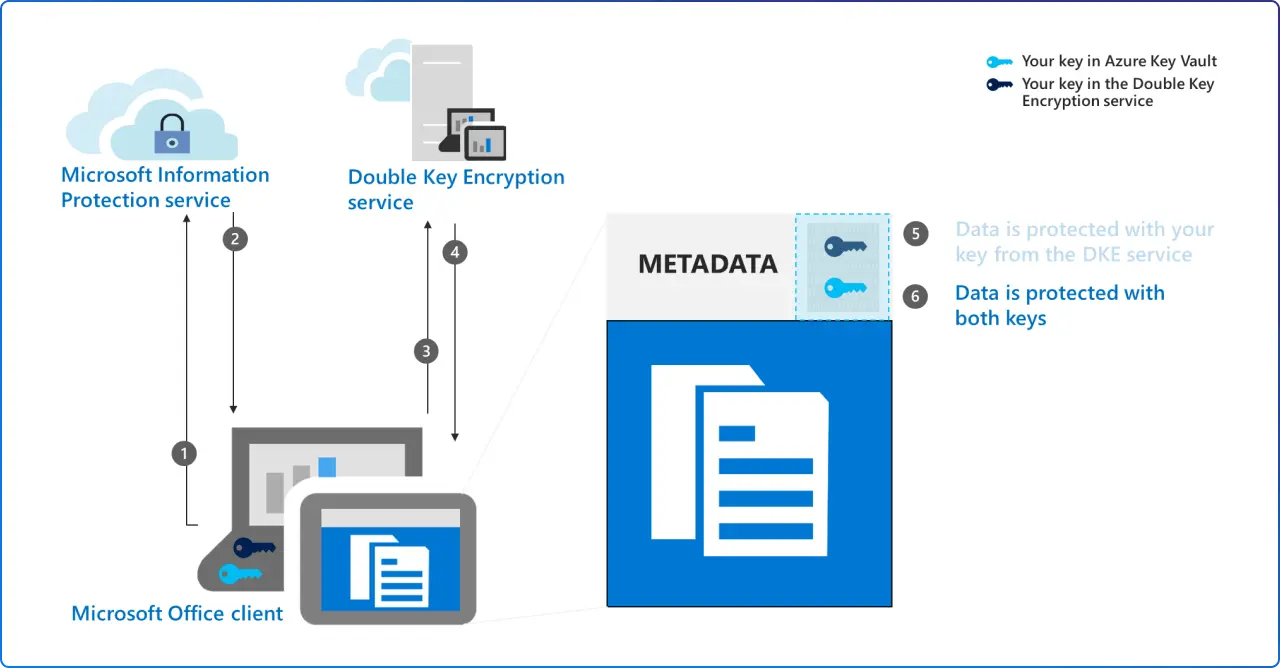
Some content is so sensitive, M&A targets, regulated health data, export‑controlled drawings, that you want the cloud provider unable to decrypt it. DKE lets you encrypt labeled files with two keys, one that you control and one that Microsoft controls, so Microsoft can’t open the content without your key. DKE works through your standard sensitivity labels, which simplifies user experience while meeting strict regulatory expectations.
As AI usage spreads, you need visibility, auditability, and policy for prompts and responses across Microsoft 365 Copilot, Security Copilot, and other AI apps. Purview’s Data Security Posture Management for AI (DSPM for AI) centralizes discovery, auditing, classification, Insider Risk, and lifecycle controls for AI interactions.
For Security Copilot specifically, Purview supports auditing, classification, Insider Risk, eDiscovery, and lifecycle management; DLP isn’t applied to those interactions today, so plan compensating controls at the endpoint and data source. Copilot experiences are also surfacing within Purview to help analysts summarize alerts and investigate faster.
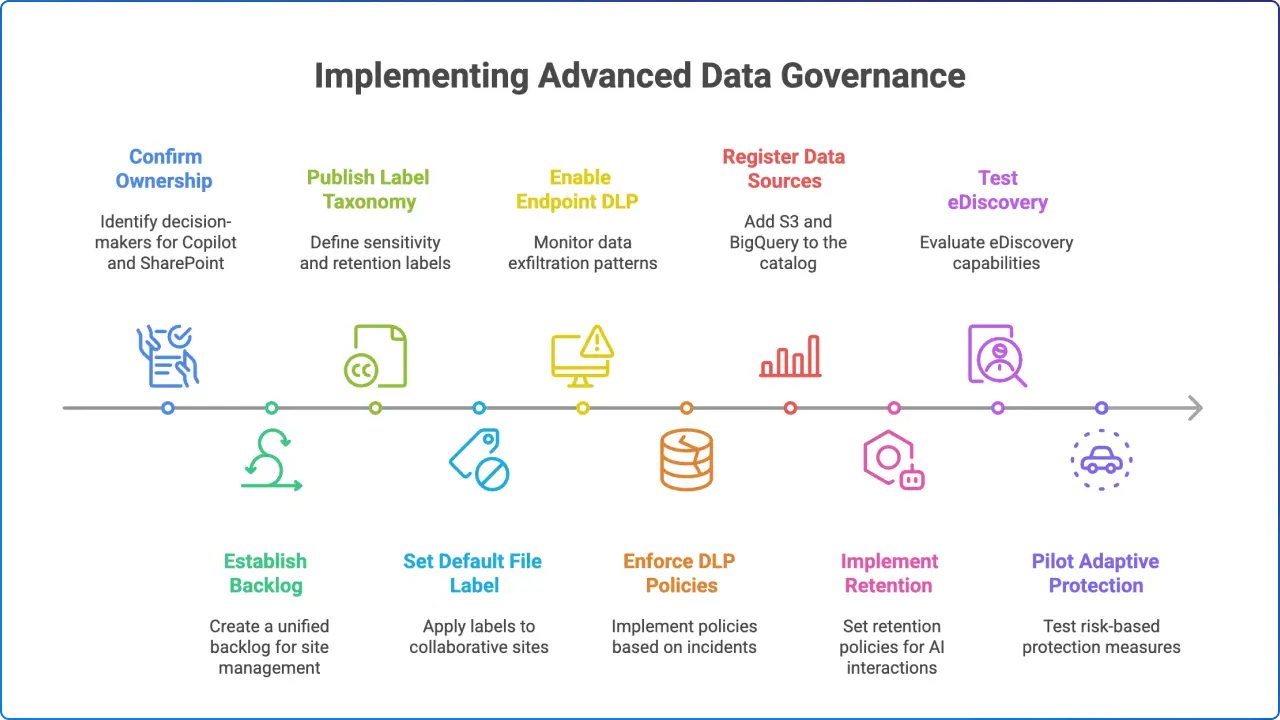
In practice, advanced governance looks like this: you label the container (team, group, or site) with the right privacy and external sharing posture; you set a default file label for the space; you enable Restricted SharePoint Search to keep Copilot focused on curated sites; you add Endpoint DLP and Adaptive Protection to turn up the controls only for risky users; and you apply retention tuned to your AI usage so prompts and responses don’t live longer than they should. You can then use eDiscovery and Communication Compliance to investigate or remediate problematic Copilot interactions when needed.
Start by defining your allowed SharePoint sites for Copilot so you can launch safely while you clean up legacy content, and publish a small, opinionated set of sensitivity labels that reflect the reality of your business today rather than an exhaustive theoretical model.
Move quickly to container labels for your most active Teams and sites so privacy and external sharing are handled by policy and not tribal knowledge. Turn on Endpoint DLP in audit‑only mode first to watch real user behavior, then ratchet up enforcement where you see risky patterns.
As you expand Copilot, create dedicated retention for AI interactions and pilot Adaptive Protection to reduce noise and user friction. Finally, add S3 or BigQuery scanning where your data actually lives to unify inventory and policy across clouds.
If you handle regulated data, lean on label‑based encryption for documents that should never leave your control and keep AI interactions on shorter retention. Use Communication Compliance and Insider Risk to monitor for inappropriate or risky prompts as a behavioral signal, not just a content one, and maintain an allowlist of sites for Copilot until your records series are fully labeled.
Compliance Manager’s multi-cloud view helps you evidence controls beyond Microsoft 365 when auditors ask about AWS or GCP workloads that feed reports back into SharePoint.
You can expect more embedded Copilot experiences inside Purview to accelerate investigations and policy tuning, reducing the time from alert to action. Microsoft is continuing to separate lifecycle controls for AI interactions so you can tune retention by AI app and scenario.
On endpoints, watch for ongoing enhancements that extend label‑based protection across more file types, making encryption and usage control feel more “ambient.” And in multi-cloud, connector breadth and data‑quality workflows for sources like Google BigQuery are maturing, which helps you bring non‑Microsoft stores into the same governance fabric. Each of these trends is already visible in current Microsoft guidance and what’s new updates.
Join Our Mailing List