
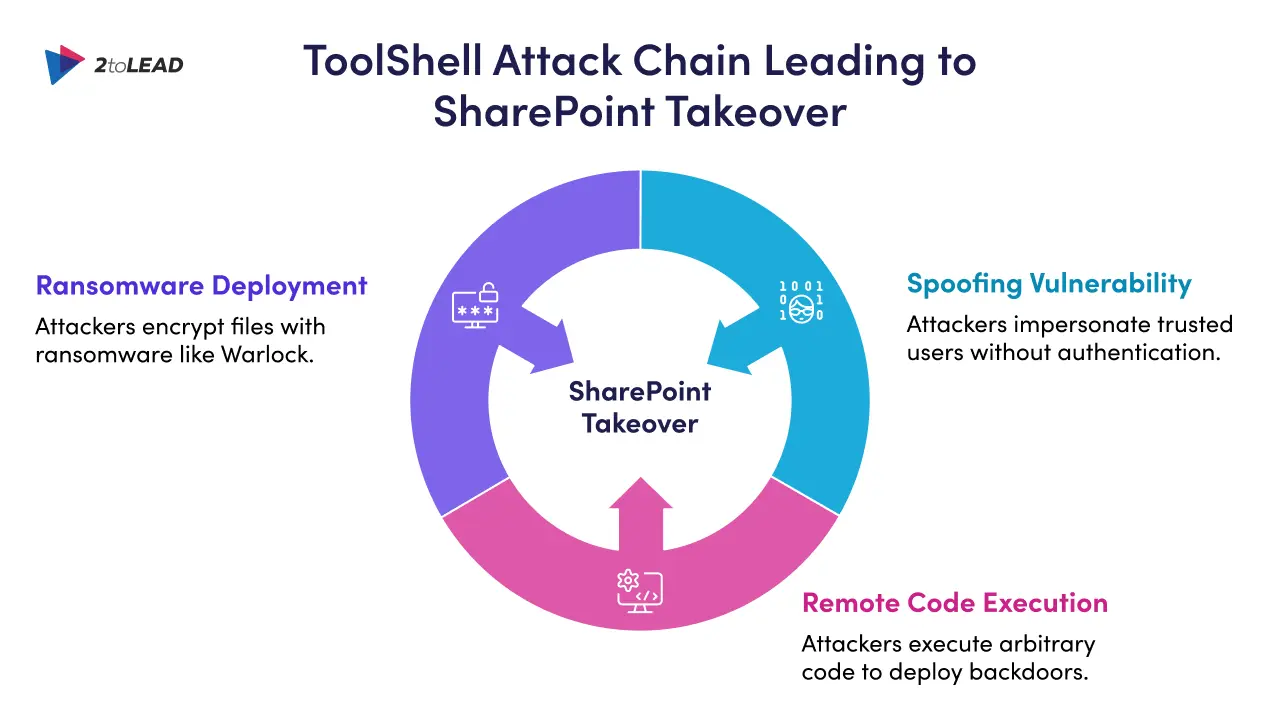
In July 2025, security researchers exposed a high-severity SharePoint vulnerability chain in on-premises Microsoft SharePoint Server dubbed ToolShell. This exploit combines two critical flaws (CVE-2025-49706 and CVE-2025-49704) to give unauthenticated attackers full control of your SharePoint environment.
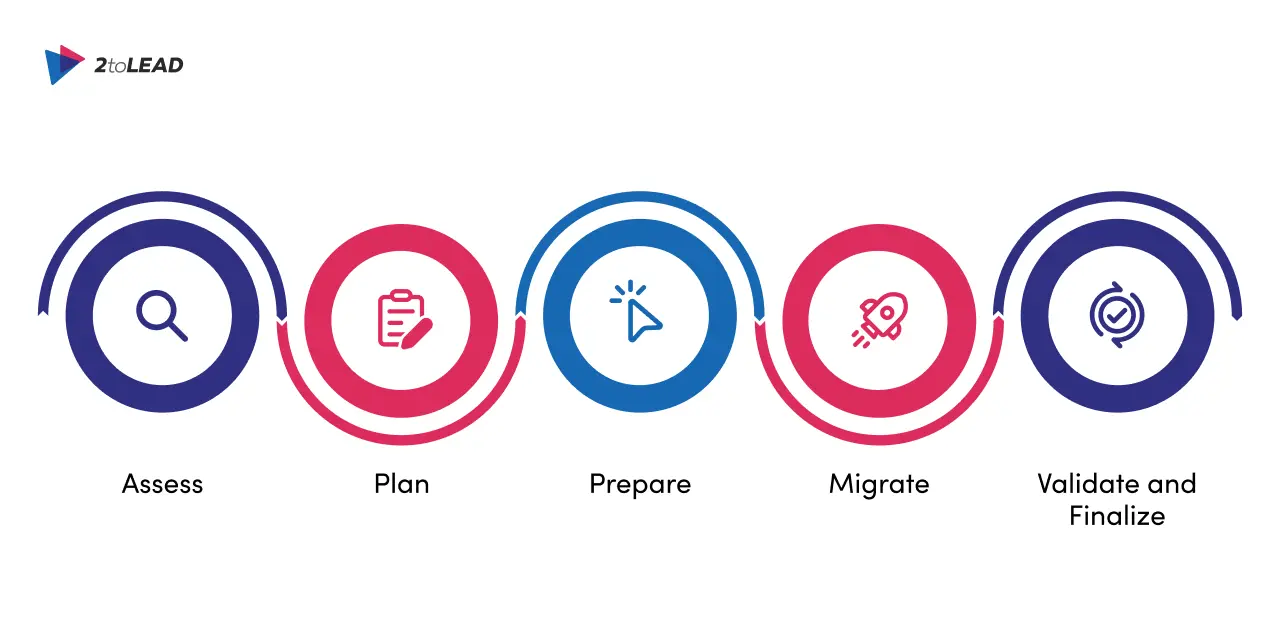
As organizations accelerate their cloud migration and SharePoint modernization journeys, this incident underscores the importance of moving to Microsoft 365 security and SharePoint Online. Before you migrate, conduct a Current Intranet Audit and build a detailed Content Inventory to identify what should be migrated, archived, or deleted. This reduces migration volume, uncovers active content owners, and helps prioritize critical content for protection.
Make migration planning part of your security posture: perform a pre-migration technical assessment and security audit of both the source environment and the target SharePoint Online configuration, and ensure you have backups and a rollback strategy in place before initiating migrations.
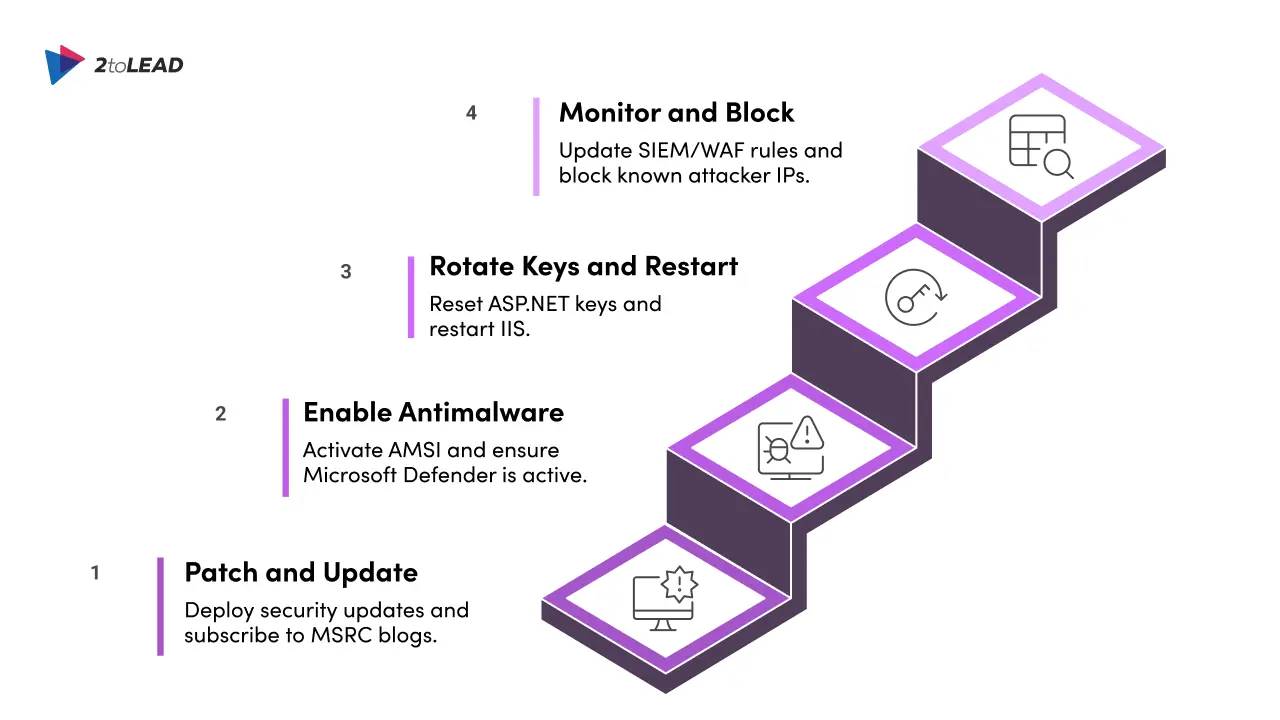
/_layouts/15/ToolPane.aspx?DisplayMode=Edit and anomalous “SignOut.aspx” referrers. Conduct a pilot migration of a small content subset and leverage delta/incremental migrations for ongoing syncs. This approach validates mappings, reduces cutover risk, and reveals performance or permissions issues before broad migration.
Moving to SharePoint Online and Microsoft 365 offers built-in safeguards that on-premises servers simply can’t match:
Prepare the target environment before migration. Establish governance, conditional access, analytics, and content monitoring so when content arrives in SharePoint Online you can immediately optimize, monitor adoption, and enforce controls.
At 2toLead, we help organizations modernize their collaboration platforms, securely and seamlessly. Our cloud migration playbooks, governance frameworks, and user-centric design ensure you:
We recommend separating migration (consolidation and cutover) from post-migration optimization. Migrate first to simplify and consolidate, then run iterative information architecture (IA) and content optimization (a Kaizen approach) so improvements are smaller, measurable, and continuous.
We also advise mapping metadata and tagging strategy before migration to preserve searchability and support better content discovery in the new environment.
👉 Let’s turn this wake-up call into your competitive edge in the Cloud Modernization era.
Join Our Newsletter