
When files, folders, or entire sites suddenly return “Access denied” after a SharePoint Online migration, the impact goes far beyond a frustrated user. It can stall projects, flood your helpdesk, and even create compliance risks. Most post‑migration access failures come from identity mapping and permission‑model translation. Detect quickly, fix at scale, and prevent repeat issues with governance.
This guide breaks down why permissions fail, how to spot issues fast, and a practical 7‑step recovery plan you can implement today plus a pre‑migration checklist to stop the problem before it starts.
Read on to take action and keep your stakeholders out of the “I can’t access the file” spiral.
Permissions break for one or more of these technical reasons:
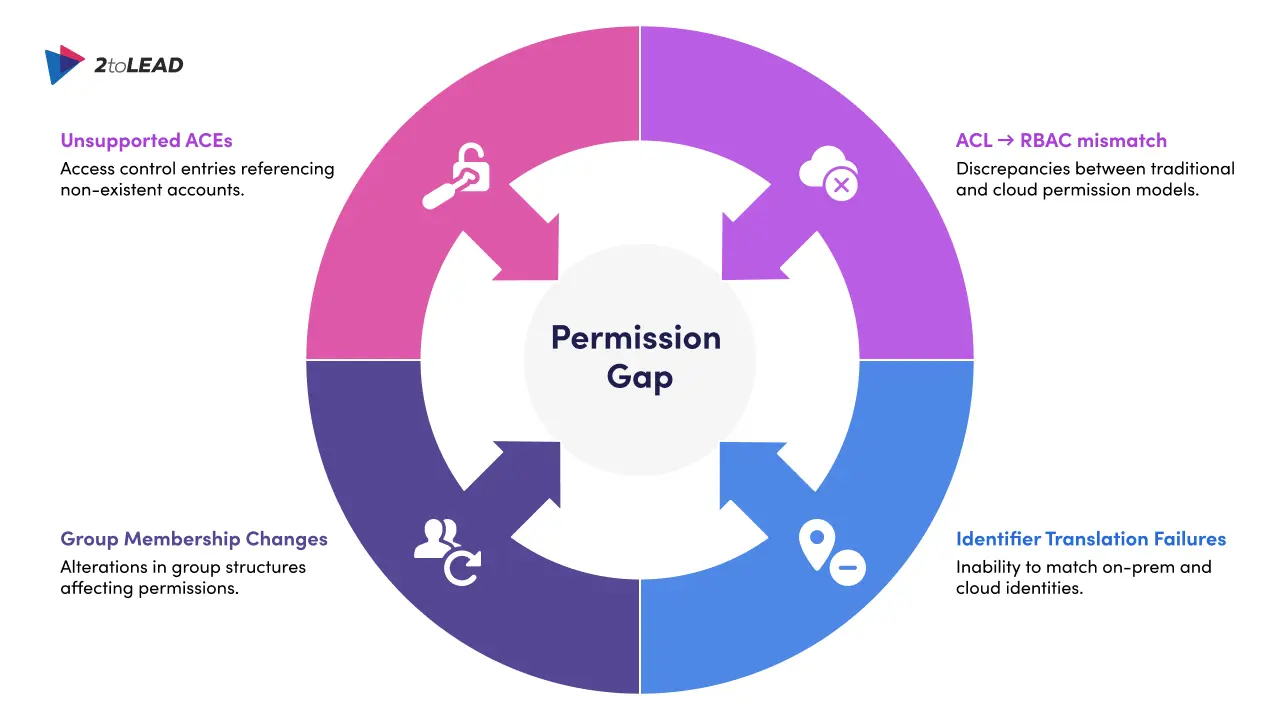
Permissions issues are more than technical headaches:
Because these impacts cascade quickly, rapid detection and remediation are business priorities, not optional cleanup tasks.
Look for these signals right away:
Fast triage tip: Export source permissions (ACLs, group membership) and destination permissions; run a quick diff for your highest‑value sites (Finance, Legal, Shared Drives). That converts noise into a finite fix list.
This is the action plan you can run now to stop the damage and restore access.
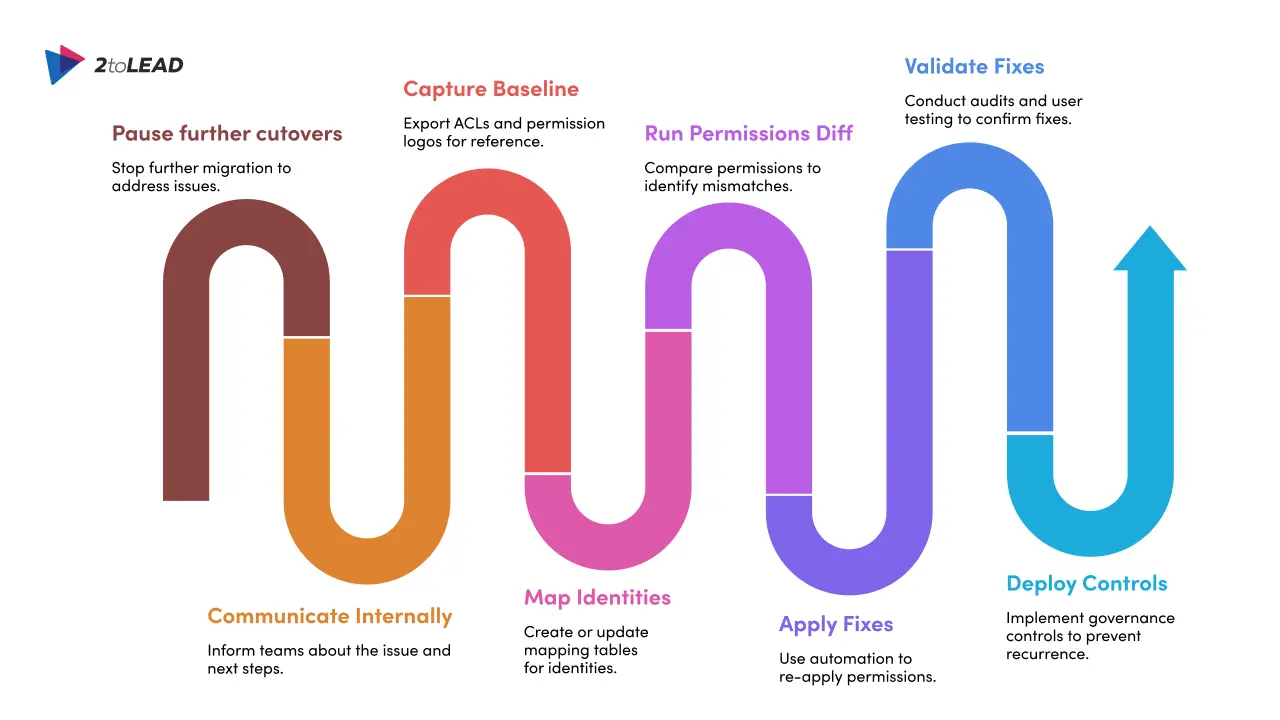
Stop additional bulk migrations for affected scopes while you triage. Send a brief internal update to affected teams explaining you’re working the issue and providing a temporary helpdesk contact and expected next steps.
Export the source ACLs, group memberships, and the migration tool’s permission logs. This snapshot is your canonical reference for reapplying or comparing permissions. You can use PowerShell (Get-ACL) exports for file shares and migration tool reports for SharePoint/OneDrive.
Create or update a mapping table (source SID/UPN → destination Entra ID/UPN). If you use a custom mapping file with Migration Manager or other tools, ensure Entra lookup settings are configured consistently with your mapping approach. Inconsistent mapping (auto-lookup + partial custom file) is a common failure point.
Use a permissions comparer or scripts to run side-by-side diffs for your highest-risk sites/folders. Prioritize business-critical areas first (finance, legal, shared team drives). This step converts tickets into a finite list of permission mismatches to fix.
For large volumes, re-apply permissions via automation rather than manual clicks. Options:
Set-ACL) or reassign group memberships in Entra/Azure AD.Always test on a small set before a broad push.
After fixes, validate using the same diff process plus live user testing: select representative users from each major group and confirm they can access required resources. Monitor helpdesk ticket volume and audit logs for a drop in “access denied” events.
Once things are stable, reduce recurrence risk by moving from manual ACEs to governed RBAC patterns where appropriate, enforcing least privilege, and using Entra ID governance features (PIM, access reviews) and sensitivity labels so permissions stay predictable. These controls make future migrations and day-to-day access management more predictable.

Get-ACL / Set-ACL): useful for file server exports and reapplying ACLs, especially when you need deterministic control at scale.If you’re about to cut over or are seeing an uptick in access issues, we can help. 2toLead offers migration permissions audits and remediation support to get users back to work quickly. Book a migration permissions review and we’ll run a targeted diff and a remediation plan for your critical sites.
Join Our Newsletter